If you have a PC with IIS installed on your Windows OS and want to engage in web designing, you may be thinking of how to ensure your web server is secure. You’re probably thinking that you can delve into the web development world and forget all about the underlying web server. Although IIS is a Microsoft product, you still have to implement security features to ensure the boost the security of your server.
It is necessary to do this as these security features frequently don‘t come configured out of the box. To ensure the security of your IIS installations, we are going to provide you in this article tips and steps you should follow to secure your IIS installations.
TIP 1: Transfer The Inetpub Folder To Another Drive
The Inetpub folder is the preset position for your website content, IIS sign-in and many more. Microsoft IIS7 and newer versions come with Inetpub folder preset on the system drive. To boost your system security, it is recommended that you lift the Inetpub folder out of that position to another partition to isolate web content from the Windows operating system. You’d commonly be required to transfer this as soon as you finish your installation.
Tip 2: Set Up Suitable IIS Modules
IIS comes with over thirty elements or modules. You don’t have to install all of them. The only ones you should install are the modules you really need for your web apps. To boost your site security, Disallow all the modules that you don’t need, to lesson to the possibility of exposing your web server to risk of hacking attacks. From time to time, you need to examine the modules you install and eliminate those that are no more required. To keep track of the modules that you install and enable, utilize the IIS Manager. to list all the modules that are enabled. To do this follows the steps below:
- Navigate to the IIS Manager and open it
- Click on the engine name to examine all the elements that come with it. Alternatively, navigate to the particular website to examine all the modules allowed for that particular site.
- Click on ‘Modules’ twice
- If you want to disable a component, click on that from the entire component list and click on ‘Remove’ from the Actions panel.
- Next, Confirm that you actually want to remove the element by clicking Yes
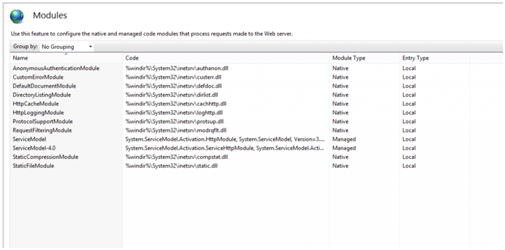
Looking at all the enabled modules from the IIS Manager
Tip 3: Disable The OPTIONS Method
The OPTIONS method offers a record of methods the web server supports. Despite the fact that this appears to be useful, it at the same time acts as a potential connection between your web server and attackers. It gives a potential attacker the information he or she requires to investigate and explore your site and discover potential ways to launch attack. Thus, it’s a good practice to disable the OPTIONS method entirely. You can do this by disallowing the OPTIONS verb from the HTTP Verb request filtering rulings in IIS. To do this:
- Go to the IIS Manager and open it
- Choose the name of the engine to set this up globally. Alternatively, alter the setting on the particular website you need to set this up on.
- Click on the ‘Request Filtering’ two times
- Move to the HTTP Verbs button
- Navigate to the Actions pane, and click on ‘Deny Verb’
- Then click on the Insert ‘OPTIONS’ in the Verb, and click OK . This will save the modifications you made.
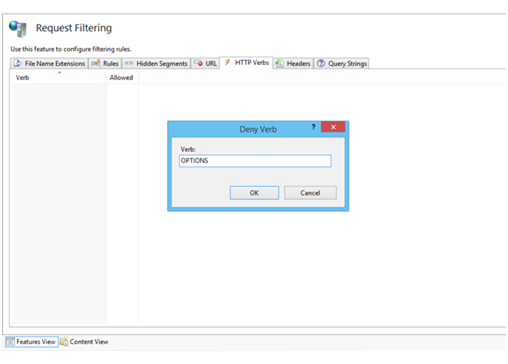
The OPTIONS method denied from the IIS Manager
TIP 4: Allow Dynamic IP Restrictions
The Dynamic IP Restrictions module makes it possible for a potential attacker to gain block access to IP addresses that process a definite number of requests and therefore, assists to inhibit Denial of Service (DoS) attacks. This component will verify the IP address of every request forwarded to the web server and go ahead to filter these queries to be able to momentarily disable IP addresses that illustrate a specific line of attack structure. You can set the Dynamic IP Restrictions component to restrict access to IP addresses after a number of simultaneous queries or by obstructing IP addresses that send out a specific amount of queries across a specific time period. What you need to do is to enable either the ‘IP Security’ feature or the “IP and Domain Restrictions”. Which one among them you enable depends on the IIS version you are working with.
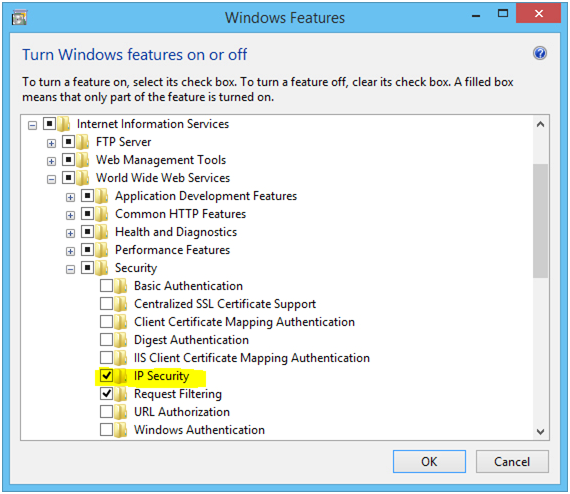
Enable the ‘IP Security’ attribute to permit for Dynamic IP Restrictions in IIS
By doing this, you’ll incorporate the ‘IP Address and Domain Restrictions component in the IIS Manager. From there, you can setup the dynamic IP restrictions can be set. Follow the steps below to achieve this:
- Go to the Open IIS Manager and press to open it
- Choose the name of the device you need to set up to enable you to set it up globally.
Alternatively, you can do by altering the particular website for which you need to set this up.
- Press on the ‘IP Address and Domain Restrictions’ twice
- Navigate to the Actions panel, choose ‘Edit Dynamic Restriction Settings’
- Alter and adjust the dynamic IP restriction settings according to your needs and click on OK to ensure you save all the changes you made.
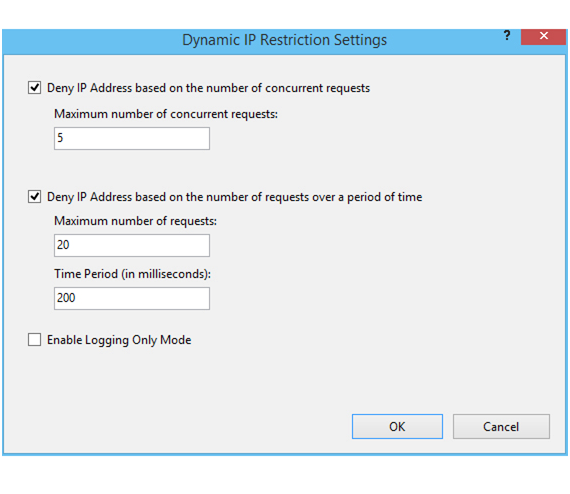
Modifying Dynamic IP Restrictions settings from the IIS Manager
Tip 5: Allow And Set Up Request Filtering Rules
It is as well a great idea to limit the types of HTTP queries the IIS process. To prevent possible injurious queries being processed, you need to configure exceptions and rulings. This is essential because IIS has the capacity to block these requests if the define the query filtering rules. For instance, you can set a rule to filter traffic that shows signs of SQL Injection trials. Although the susceptibility of SQL Injection ought to be set at a foundation, filtering for SQL Injection attacks is essential for minimizing such attacks. You can normally set this from the Rules button you’ll see in the Request Filtering interface of the IIS Manager. To do this, follow the steps below:
- Click to open the IIS Manager
- Click on the name of the device for which you want to set it up for to set it up globally or modify the settings in the particular website for which you require to set this up. To do this, follow the steps below:
- Click on ‘Request Filtering’ twice
- Alter the Rules button
- Go to the Actions panel, choose ‘Integrate Filtering Rule’
- Configure the needed rules, and click on OK to ensure you save the changes you have made.
The rule configured in the following screenshot would direct IIS to look for the offered threads the query for .asp and .aspx pages. This would direct IIS to obstruct the query from any threads like this whenever they are observed.
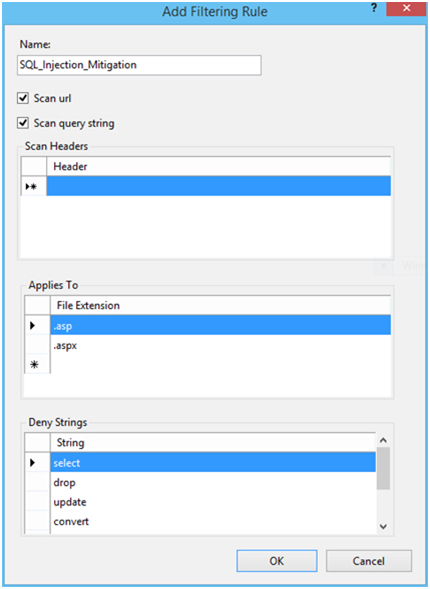
Configuring Request filtering rule to investigate for SQL Injection attacks
Besides, you can filter requests that are made up of features like high-bit scripts or double escape scripts.
Tip 6: Allow Logging Attribute
Setting up IIS logging will make IIS log data from HTTP query that comes from the server. This is a great help and can help you understand issues that may have happened on your website if you run into problems. You can as well monitor the logs stored by your server constantly or at intervals to verify how your server is performing and give you an idea when you need to optimize for more security features.
This can be automated with the use of server verification tools. Therefore, it is essential to back up your server’s logs.
Microsoft additionally offers the Log Parser tool to help you query and salvage particular data from IIS logs. Furthermore, log consolidation tools are very essential for strengthening consolidating and archiving data obtain from server logs in a more significant manner.
IIS logging can be allowed and set up IIS Manager. From the manager click on the name of the device you are configuring the feature for and then click on Logging. Given that, these logs files can be enormous, it is advisable to open a new file from time to time.
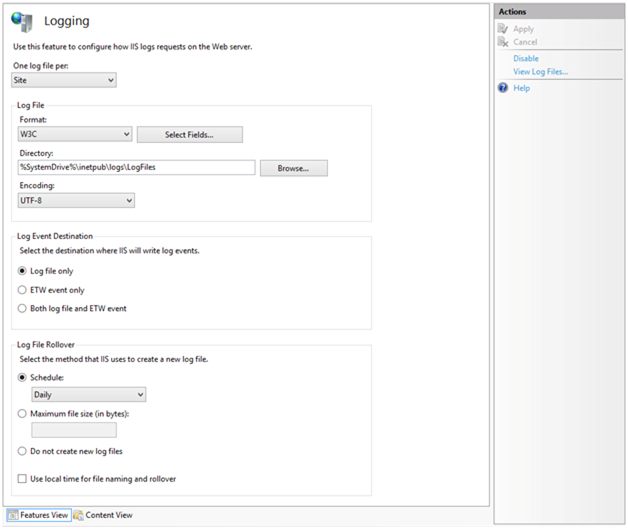
Enabling Logging options in IIS
Tip 7: Make use of the Security Configuration Wizard (SCW) and the Security Compliance Manager (SCM)
These are two tools provided by Microsoft to help you verify the security of your IIS installations. The Security Configuration Wizard (SCW) carries out various investigations and offers suggestions on the way you can harden the security of your web servers.
The Security Compliance Manager (SCM) instrument, on the other hand, carry out security checks and investigations on your server and make a comparison of your server settings to the preset templates required for every industry standard and suggestions made in the security guide.
The Microsoft Security Compliance Manager (SCM) appliance
Lastly: Keep Your Web Server Constantly Updated
Lastly, ensure you constantly update your web server to ensure it has all the latest updates and security patches. Very often, we overlook and neglect this basic security essential but it is highly necessary. The larger part of server attacks recorded frequently happens on servers that are not properly patched.
This is an indication that keeping your web server up to date is a highly essential security tip to implement. The majority of hacks affecting the web server occur on unpatched servers. This just demonstrates how important it is to always keep your IIS web server up to date.
Check out these top 3 Best web hosting services
0