Introduction Let’s Encrypt is a free, reliable, and automated Certificate Authority (CA) designed by the non-profit Internet Security Research Group (ISRG). The CA utilizes fully automated processes to deliver free... Read more
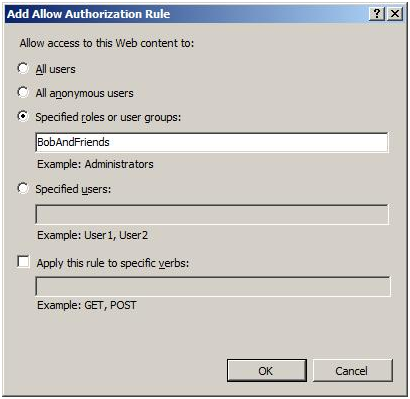
In the former IIS versions, it was pretty difficult to carry out authorization. Due to the reason that IIS worked with only the identities of Windows. You would have to... Read more
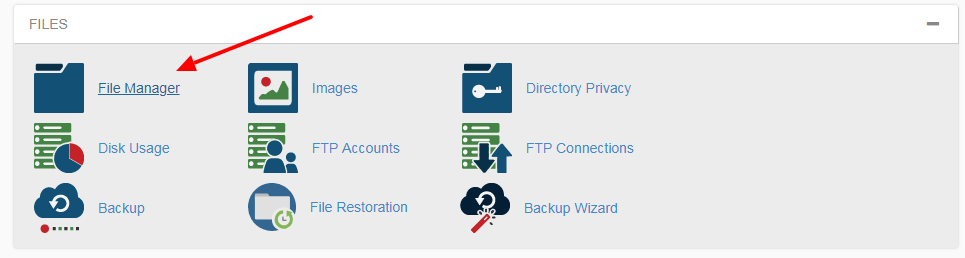
Code injection through a backdoor has become so familiar, and millions of websites get hacked every year. It’s vital to do everything you can to protect your website. For a... Read more
We, the Tecmint Team is consistent in producing high quality articles of all kinds in Linux and Open-source domain. We have been working hard from the first day of our... Read more
In this short article, we will walk newbies through the various simple ways of checking system timezone in Linux. Time management on a Linux machine especially a production server is... Read more
Process management is one of the important aspects of System Administration in Linux, and it includes killing of processes using the kill command. Find and Kill Running Processes in Linux... Read more
For all those people who like to use Twitter in console/terminal rather than Graphical User Interface can now access their twitter account right from the Linux Console. Yes you heard... Read more
You should always be concerned about the security of your website infrastructure. It is essential. Your website maintenance must include ways to secure your site infrastructure and PHP applications. The... Read more
In this tutorial we will learn how to install local software packages (.DEB) in Debian and its derivatives such as Ubuntu and Linux Mint using three different command line tools... Read more
Usually, to delete/remove a file from Linux terminal, we use the rm command (delete files), shred command (securely delete a file), wipe command (securely erase a file) or secure-deletion toolkit... Read more
