Using a Different System?
-
How to Enable TLS 1.3 in Nginx on Ubuntu 18.04 LTS
-
How to Enable TLS 1.3 in Nginx on FreeBSD 12
-
How to Enable TLS 1.3 in Apache on FreeBSD 12
-
How to Enable TLS 1.3 in Nginx on Fedora 29
-
How to Enable TLS 1.3 in Nginx on Debian 9
-
How to Enable TLS 1.3 in Apache on Debian 10
TLS 1.3 is a version of the Transport Layer Security (TLS) protocol that was published in 2018 as a proposed standard in RFC 8446. It offers security and performance improvements over its predecessors.
This guide will demonstrate how to enable TLS 1.3 using the Apache web server on Fedora 30.
Requirements
- Vultr Cloud Compute (VC2) instance running Fedora 30.
- A valid domain name and properly configured
A/AAAA/CNAMEDNS records for your domain. - A valid TLS certificate. We will get one from Let’s Encrypt.
- Apache version
2.4.36or greater. - OpenSSL version
1.1.1or greater.
Before you begin
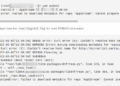
Check the Fedora version.
cat /etc/fedora-release
# Fedora release 30 (Thirty)
Create a new non-root user account with sudo access and switch to it.
useradd -c "John Doe" johndoe && passwd johndoe
usermod -aG wheel johndoe
su - johndoe
NOTE: Replace johndoe with your username.
Set up the timezone.
timedatectl list-timezones
sudo timedatectl set-timezone 'Region/City'
Ensure that your system is up to date.
sudo dnf check-upgrade || sudo dnf upgrade -y
Install the needed packages.
sudo dnf install -y socat git
Disable SELinux and Firewall.
sudo setenforce 0 ; sudo systemctl stop firewalld ; sudo systemctl disable firewalld
Install the acme.sh client and obtain a TLS certificate from Let’s Encrypt
Install acme.sh.
sudo mkdir /etc/letsencrypt
git clone https://github.com/Neilpang/acme.sh.git
cd acme.sh
sudo ./acme.sh --install --home /etc/letsencrypt --accountemail [email protected]
cd ~
source ~/.bashrc
Check the version.
/etc/letsencrypt/acme.sh --version
# v2.8.2
Obtain RSA and ECDSA certificates for your domain.
# RSA
sudo /etc/letsencrypt/acme.sh --issue --standalone -d example.com --ocsp-must-staple --keylength 2048
# ECC/ECDSA
sudo /etc/letsencrypt/acme.sh --issue --standalone -d example.com --ocsp-must-staple --keylength ec-256
NOTE: Replace example.com in commands with your domain name.
Create sensible directories to store your certs and keys in. We will use /etc/letsencrypt.
sudo mkdir -p /etc/letsencrypt/example.com
sudo mkdir -p /etc/letsencrypt/example.com_ecc
Install and copy certificates to /etc/letsencrypt.
# RSA
sudo /etc/letsencrypt/acme.sh --install-cert -d example.com --cert-file /etc/letsencrypt/example.com/cert.pem --key-file /etc/letsencrypt/example.com/private.key --fullchain-file /etc/letsencrypt/example.com/fullchain.pem
# ECC/ECDSA
sudo /etc/letsencrypt/acme.sh --install-cert -d example.com --ecc --cert-file /etc/letsencrypt/example.com_ecc/cert.pem --key-file /etc/letsencrypt/example.com_ecc/private.key --fullchain-file /etc/letsencrypt/example.com_ecc/fullchain.pem
After running the above commands, your certificates and keys will be in the following locations:
- RSA:
/etc/letsencrypt/example.com - ECC/ECDSA:
/etc/letsencrypt/example.com_ecc
Install Apache
Apache added support for TLS 1.3 in version 2.4.36. Fedora 30 system comes with Apache and OpenSSL that support TLS 1.3 out of the box, so there is no need to build a custom version.
Download and install the latest 2.4 branch of Apache and its module for SSL via the dnf package manager.
sudo dnf install -y httpd mod_ssl
Check the version.
sudo httpd -v
# Server version: Apache/2.4.39 (Fedora)
# Server built: May 2 2019 14:50:28
Start and enable Apache.
sudo systemctl start httpd.service
sudo systemctl enable httpd.service
Configure Apache for TLS 1.3
Now that we have successfully installed Apache, we are ready to configure it to start using TLS 1.3 on our server.
Run sudo vim /etc/httpd/conf.d/example.com.conf, and populate the file with the following basic configuration.
<IfModule mod_ssl.c>
<VirtualHost *:443>
ServerName example.com
SSLEngine on
SSLProtocol all -SSLv2 -SSLv3
# RSA
SSLCertificateFile "/etc/letsencrypt/example.com/fullchain.pem"
SSLCertificateKeyFile "/etc/letsencrypt/example.com/private.key"
# ECC
SSLCertificateFile "/etc/letsencrypt/example.com_ecc/fullchain.pem"
SSLCertificateKeyFile "/etc/letsencrypt/example.com_ecc/private.key"
</VirtualHost>
</IfModule>
Save the file and exit.
Check the configuration.
sudo apachectl configtest
Reload Apache to activate the new configuration.
sudo systemctl reload httpd.service
Open your site via HTTPS protocol in your web browser. To verify TLS 1.3, you can use browser dev tools or SSL Labs service. The screenshots below show Chrome’s security tab with TLS 1.3 in action.


You have successfully enabled TLS 1.3 in Apache on your Fedora 30 server. The final version of TLS 1.3 was defined in August 2018, so there’s no better time to start adopting this new technology.
Want to contribute?
You could earn up to $300 by adding new articles
Suggest an update
Request an article