Introduction to Fail2Ban
By default, a client connects to SSH using port 22. Because this is a well-known port, the default configuration is vulnerable to many brute force attacks. Fail2Ban is a solution to automatically protect a server from these attacks. The program runs in background, scans the log files to detect which IPs are attacking and automatically bans them from accessing SSH.
Installing Fail2Ban
In this tutorial, we will install Fail2Ban on CentOS 6 through the EPEL repository. Run the following commands.
yum install epel-release
yum install fail2ban
Explanation
yum install epel-release: Installs the EPEL repository (Extra Packages for Enterprise Linux).yum install fail2ban: Installs Fail2Ban from the EPEL repository.
Configuring the Fail2Ban settings
Open the Fail2Ban configuration file.
nano /etc/fail2ban/jail.conf
In the file, you will see some parameters as shown below. Adjust any of the values to your needs.
[DEFAULT]
# "ignoreip" can be an IP address, a CIDR mask or a DNS host. Fail2ban will not
# ban a host which matches an address in this list. Several addresses can be
# defined using space separator.
ignoreip = 127.0.0.1
# "bantime" is the number of seconds that a host is banned.
bantime = 600
# A host is banned if it has generated "maxretry" during the last "findtime"
# seconds.
findtime = 600
# "maxretry" is the number of failures before a host get banned.
maxretry = 3
Explanation
ignoreip: Don’t ban hosts which match an address in this list. Several addresses can be defined using space separator. Write your personal IP on this line.bantime: The number of seconds that a host is banned.findtime: A host is banned if it has generatedmaxretryduring the lastfindtime.maxretry: The number of failures before a host get banned.
Configuring Fail2Ban to protect SSH
First, we need to create a configuration file.
nano /etc/fail2ban/jail.local
Copy the lines below and paste to the file.
[ssh-iptables]
enabled = true
filter = sshd
action = iptables[name=SSH, port=ssh, protocol=tcp]
# sendmail-whois[name=SSH, dest=root, [email protected]]
logpath = /var/log/secure
maxretry = 5
enabled: Activate the protection. If you want to turn it off, change the value to false.filter: By default, it is set to sshd which refers to the file/etc/fail2ban/filter.d/sshd.conf.action: Fail2Ban will ban the IP that matches the filter/etc/fail2ban/action.d/iptables.conf. If you had changed the SSH port before, changeport=sshto the new port, for exampleport=2222. If you are using port 22, you won’t need to change the value.logpath: The path of the log file used by Fail2Ban.maxretry: The maximum number of failed login attempts.
Starting up Fail2Ban service
Run these two commands below to start the Fail2Ban service:
chkconfig --level 23 fail2ban on
service fail2ban start
Finally, check iptables to see if it has the rules added by Fail2Ban.
iptables -L
The result will look similar to this output.
Chain INPUT (policy ACCEPT)
target prot opt source destination
f2b-SSH tcp -- anywhere anywhere tcp dpt:EtherNet/IP-1
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain f2b-SSH (1 references)
target prot opt source destination
RETURN all -- anywhere anywhere
How to track failed login attempts
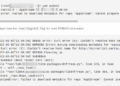
You can use this command to check if your server has had failed login attempts (possible attacks).
cat /var/log/secure | grep 'Failed password'
The result will look similar to these lines.
Dec 6 22:47:12 vultr sshd[7942]: Failed password for root from 43.229.53.67 port 23021 ssh2
Dec 6 22:47:15 vultr sshd[7944]: Failed password for root from 43.229.53.67 port 40996 ssh2
Dec 6 22:47:16 vultr sshd[7944]: Failed password for root from 43.229.53.67 port 40996 ssh2
Dec 6 22:47:18 vultr sshd[7944]: Failed password for root from 43.229.53.67 port 40996 ssh2
Dec 6 22:47:31 vultr sshd[7948]: Failed password for root from 43.229.53.67 port 29907 ssh2
Dec 6 22:47:34 vultr sshd[7948]: Failed password for root from 43.229.53.67 port 29907 ssh2
Dec 6 22:47:36 vultr sshd[7948]: Failed password for root from 43.229.53.67 port 29907 ssh2
Dec 6 22:47:39 vultr sshd[7950]: Failed password for root from 43.229.53.67 port 48386 ssh2
Dec 6 22:47:41 vultr sshd[7950]: Failed password for root from 43.229.53.67 port 48386 ssh2
Dec 6 22:47:43 vultr sshd[7950]: Failed password for root from 43.229.53.67 port 48386 ssh2
Dec 6 22:47:47 vultr sshd[7952]: Failed password for root from 43.229.53.67 port 62846 ssh2
Dec 6 22:47:49 vultr sshd[7952]: Failed password for root from 43.229.53.67 port 62846 ssh2
To view which IPs have been banned, use the following command.
iptables -L -n
To delete an IP address from banned list, run the following command. Change banned_ip to the IP that you want to unban.
iptables -D f2b-SSH -s banned_ip -j DROP
Want to contribute?
You could earn up to $300 by adding new articles
Suggest an update
Request an article