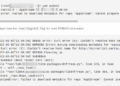
Vultr offers you awesome private network connectivity for servers running at the same location. But sometimes you want two servers in different countries / datacenters to be able to communicate in a private and secure way. This tutorial will show you how to achieve that with the help of OpenVPN. The operating systems used here are Debian and CentOS, just to show you two different configurations. This can be easily adapted for Debian -> Debian, Ubuntu -> FreeBSD and so on.
- Machine 1: Debian, will act as server (Location: NL)
- Machine 2: CentOS, will act as client (Location: FR)
Machine 1
Start on machine 1 by installing OpenVPN:
apt-get install openvpn
Then, copy the example configuration and the tool for generating keys, easy-rsa, to /etc/openvpn:
cp -r /usr/share/doc/openvpn/examples/easy-rsa/ /usr/share/doc/openvpn/examples/sample-config-files/server.conf.gz /etc/openvpn
The default values for your keys aren’t exactly safe anymore, to fix this open /etc/openvpn/easy-rsa/2.0/vars with your favorite text editor and modify the following line:
export KEY_SIZE=4096
Next, ensure that the values are loaded into your current session, clean up eventually existing keys, and generate your certificate authority:
cd /etc/openvpn/easy-rsa/2.0
source ./vars
./clean-all
./build-ca
You will be prompted for information. Make your life easier by supplying information about your server, for example, where it’s located and what the FQDN is/will be. This is useful for when you have to debug problems:
Country Name (2 letter code) [US]:NL
State or Province Name (full name) [CA]:-
Locality Name (eg, city) [SanFrancisco]:Vultr Datacenter NL
Organization Name (eg, company) [Fort-Funston]:-
Organizational Unit Name (eg, section) [changeme]:-
Common Name (eg, your name or your server's hostname) [changeme]:yourserver1.yourdomain.tld
Name [changeme]:-
Email Address [[email protected]]:[email protected]
Another necessity is parameters for the Diffie-Hellman key exchange. Those need to be generated too:
./build-dh
Important: The build-dh command is a relatively complex process that can take up to ten minutes, depending on your server’s resources.
To further improve the security of this connection, we will generate a static secret that needs to be distributed amongst all clients:
mkdir /etc/openvpn/keys
openvpn --genkey --secret /etc/openvpn/keys/ta.key
Now, you can generate the key for the server:
./build-key-server server1
This command will prompt for some information:
Country Name (2 letter code) [US]:NL
State or Province Name (full name) [CA]:-
Locality Name (eg, city) [SanFrancisco]:Vultr Datacenter NL
Organization Name (eg, company) [Fort-Funston]:-
Organizational Unit Name (eg, section) [changeme]:-
Common Name (eg, your name or your server's hostname) [server1]:yourserver1.yourdomain.tld
Name [changeme]:-
Email Address [[email protected]]:[email protected]
The final step is to sign the certificate request that was just generated with the CA’s key:
1 out of 1 certificate requests certified, commit? [y/n]y
Copy the necessary keys and certificates into a separate folder:
cd /etc/openvpn/easy-rsa/2.0/keys
cp dh4096.pem ca.crt server1.crt server1.key /etc/openvpn/keys/
chmod 700 /etc/openvpn/keys
chmod 600 /etc/openvpn/keys/*
Now for the configuration, unzip it …
cd /etc/openvpn
gunzip server.conf.gz
… and open the resulting server.conf with your favorite text editor. The configuration should look similar to this:
port 1194
proto udp
dev tun
ca keys/ca.crt
cert keys/server1.crt
key keys/server1.key
dh keys/dh4096.pem
server 10.8.100.0 255.255.255.0
ifconfig-pool-persist ipp.txt
# Uncomment this if you have multiple clients
# and want them to be able to see each other
;client-to-client
keepalive 10 120
tls-auth keys/ta.key 0
tls-cipher DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-CAMELLIA256-SHA:DHE-RSA-AES256-SHA:DHE-RSA-CAMELLIA128-SHA:DHE-RSA-AES128-SHA:CAMELLIA256-SHA:AES256-SHA:CAMELLIA128-SHA:AES128-SHA
cipher AES-256-CBC
auth SHA384
comp-lzo
user nobody
group nogroup
persist-key
persist-tun
verb 3
mute 20
After restarting the service you should watch your log a bit …
service openvpn restart && tail -f /var/log/syslog
… to make sure everything is working. If no errors are detected, then you can generate the keys for your second server:
cd /etc/openvpn/easy-rsa/2.0
source ./vars
./build-key server2
Again, you will be prompted for information:
Country Name (2 letter code) [US]:FR
State or Province Name (full name) [CA]:-
Locality Name (eg, city) [SanFrancisco]:Vultr Datacenter FR
Organization Name (eg, company) [Fort-Funston]:-
Organizational Unit Name (eg, section) [changeme]:-
Common Name (eg, your name or your server's hostname)
[server2]:yourserver2.yourdomain.tld
Name [changeme]:-
Email Address [[email protected]]:[email protected]
Now, you need to transfer the necessary files to your second server, preferably encrypted:
cd /etc/openvpn/easy-rsa/2.0/keys
cp /etc/openvpn/keys/ta.key .
tar -cf vpn.tar ca.crt server2.crt server2.key ta.key
scp vpn.tar yourusername@server2:~/
rm vpn.tar
Machine 2
Time to switch to the SSH-connection of your second server. The first step is to install OpenVPN …
yum install openvpn
… and to deactivate firewalld. The replacement will be plain iptables.
systemctl stop firewalld
systemctl disable firewalld
Unpack the archive that you just moved to the server and properly set permissions on the files:
cd /etc/openvpn
mkdir keys
chmod 700 keys
cd keys
tar -xf ~/vpn.tar -C .
chmod 600 *
Create /etc/openvpn/client.conf with your favorite text editor. It should look like this:
client
dev tun
proto udp
remote yourserver yourport
resolv-retry infinite
nobind
user nobody
group openvpn
persist-key
persist-tun
ca keys/ca.crt
cert keys/server2.crt
key keys/.key
ns-cert-type server
tls-auth keys/ta.key 1
tls-cipher DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-CAMELLIA256-SHA:DHE-RSA-AES256-SHA:DHE-RSA-CAMELLIA128-SHA:DHE-RSA-AES128-SHA:CAMELLIA256-SHA:AES256-SHA:CAMELLIA128-SHA:AES128-SHA
cipher AES-256-CBC
auth SHA384
remote-cert-tls server
comp-lzo
verb 3
mute 20
The last step is to start and enable the service:
systemctl start [email protected]
systemctl enable [email protected]
If everything is working, then you should have no problem pinging the first server:
PING 10.8.100.1 (10.8.100.1) 56(84) bytes of data.
64 bytes from 10.8.100.1: icmp_seq=1 ttl=64 time=17.8 ms
64 bytes from 10.8.100.1: icmp_seq=2 ttl=64 time=17.9 ms
64 bytes from 10.8.100.1: icmp_seq=3 ttl=64 time=17.8 ms
You now have a private connection over the Internet!
If you need to troubleshoot any errors, try checking the logs with the following command:
journalctl -xn
Want to contribute?
You could earn up to $300 by adding new articles
Suggest an update
Request an article