Install Let's Encrypt to Create SSL Certificates

Let’s Encrypt is an SSL certificate authority managed by the Internet Security Research Group (ISRG). It utilizes the Automated Certificate Management Environment (ACME) to automatically deploy free SSL certificates that are trusted by nearly all major browsers.
Note
For most situations, the recommended method for installing Let’s Encrypt certificates is the official Certbot tool. Certbot automates the process of obtaining and installing a certificate, and can also automatically update your web server configuration. The instructions in this guide install Let’s Encrypt and add certificates manually, which is not necessary for most users.
Before you Begin
-
Familiarize yourself with our Getting Started guide and complete the steps for setting your Linode’s hostname and timezone.
-
Complete the steps in our Securing Your Server guide to create a standard user account, harden SSH access, and remove unnecessary network services.
-
Update your server’s software packages:
CentOS
sudo yum update && sudo yum upgradeDebian / Ubuntu
sudo apt update && sudo apt upgradeNote
This guide is written for a non-root user. Commands that require elevated privileges are prefixed withsudo. If you’re not familiar with thesudocommand, you can check our Users and Groups guide.
Download and Install Let’s Encrypt
-
Install the
gitpackage:CentOS
sudo yum install gitDebian / Ubuntu
sudo apt-get install git -
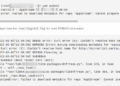
Download a clone of Let’s Encrypt from the official GitHub repository.
/optis a common installation directory for third-party packages, so let’s install the clone to/opt/letsencrypt:sudo git clone https://github.com/letsencrypt/letsencrypt /opt/letsencrypt -
Navigate to the new
/opt/letsencryptdirectory:cd /opt/letsencrypt
Create an SSL Certificate
Let’s Encrypt automatically performs Domain Validation (DV) using a series of challenges. The Certificate Authority (CA) uses challenges to verify the authenticity of your computer’s domain. Once your Linode has been validated, the CA will issue SSL certificates to you.
-
Run Let’s Encrypt with the
--standaloneparameter. For each additional domain name requiring a certificate, add-d example.comto the end of the command.sudo -H ./letsencrypt-auto certonly --standalone -d example.com -d www.example.comNote
Let’s Encrypt does not deploy wildcard certificates. Each subdomain requires its own certificate. -
When prompted, specify an administrative email address. This will allow you to regain control of a lost certificate and receive urgent security notices if necessary. Press ENTER or RETURN to save.
-
Agree to the Terms of Service and specify if you would like to share your email address with EFF:
------------------------------------------------------------------------------- Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must agree in order to register with the ACME server at https://acme-v01.api.letsencrypt.org/directory ------------------------------------------------------------------------------- (A)gree/(C)ancel: a ------------------------------------------------------------------------------- Would you be willing to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about EFF and our work to encrypt the web, protect its users and defend digital rights. ------------------------------------------------------------------------------- (Y)es/(N)o: n -
If all goes well, a message similar to the one below will appear. Its appearance means Let’s Encrypt has approved and issued your certificates.
IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/example.com/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/example.com/privkey.pem Your cert will expire on 2018-05-27. To obtain a new or tweaked version of this certificate in the future, simply run letsencrypt-auto again. To non-interactively renew *all* of your certificates, run "letsencrypt-auto renew" - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le
Check Certificate Domains
-
The output of the Let’s Encrypt script shows where your certificate is stored; in this case,
/etc/letsencrypt/live:sudo ls /etc/letsencrypt/liveexample.com -
All of the domains you specified above will be covered under this single certificate. This can be verified as follows:
./certbot-auto certificatesFound the following certs: Certificate Name: example.com Domains: example.com www.example.com Expiry Date: 2018-05-27 20:49:02+00:00 (VALID: 89 days) Certificate Path: /etc/letsencrypt/live/example.com/fullchain.pem Private Key Path: /etc/letsencrypt/live/example.com/privkey.pem
Maintenance
Renew SSL Certificates
-
Return to the
/opt/letsencryptdirectory:cd /opt/letsencrypt -
Execute the command you used in Step 1 of the Create an SSL Certificate section, adding the
--renew-by-defaultparameter:sudo -H ./letsencrypt-auto certonly --standalone --renew-by-default -d example.com -d www.example.com -
After a few moments, a confirmation similar to the one below should appear:
IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/example.com/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/example.com/privkey.pem Your cert will expire on 2018-05-27. To obtain a new or tweaked version of this certificate in the future, simply run letsencrypt-auto again. To non-interactively renew *all* of your certificates, run "letsencrypt-auto renew" - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-leLet’s Encrypt has refreshed the lifespan of your certificates; in this example, March 31st, 2016 is the new expiration date.
Note
Let’s Encrypt certificates have a 90-day lifespan. According to Let’s Encrypt, this encourages automation and minimizes damage from key compromises. You can renew your certificates at any time during their lifespan.
Automatically Renew SSL Certificates (Optional)
You can also automate certificate renewal. This will prevent your certificates from expiring, and can be accomplished with cron.
-
The output of the previous command shows how to non-interactively renew all of your certificates:
./letsencrypt-auto renew -
Set this task to run automatically once per month using a cron job:
sudo crontab -eAdd the following line to the end of the crontab file:
- crontab
-
10 0 1 * * /opt/letsencrypt/letsencrypt-auto renew
Update Let’s Encrypt
-
Return to the
/opt/letsencryptdirectory:cd /opt/letsencrypt -
Download any changes made to Let’s Encrypt since you last cloned or pulled the repository, effectively updating it:
sudo git pull
Automatically Update Let’s Encrypt (Optional)
You can also use cron to keep the letsencrypt-auto client up to date.
sudo crontab -e
- crontab
-
10 0 1 * * cd /opt/letsencrypt && git pull
More Information
You may wish to consult the following resources for additional information on this topic. While these are provided in the hope that they will be useful, please note that we cannot vouch for the accuracy or timeliness of externally hosted materials.
- Let’s Encrypt Homepage
Join our Community
Find answers, ask questions, and help others.
This guide is published under a CC BY-ND 4.0 license.