
Use One-Time Passwords for Two-Factor Authentication with SSH on Ubuntu 16.04 and Debian 8 In this guide, you’ll learn how to use one-time passwords for two-factor authentication with SSH on... Read more
ccat is command line similar to cat command in Linux that displays the content of a file with syntax highlighting for the following programming languages: Javascript, Java, Go, Ruby, C,... Read more

Install Let's Encrypt to Create SSL Certificates Let’s Encrypt is an SSL certificate authority managed by the Internet Security Research Group (ISRG). It utilizes the Automated Certificate Management Environment (ACME)... Read more
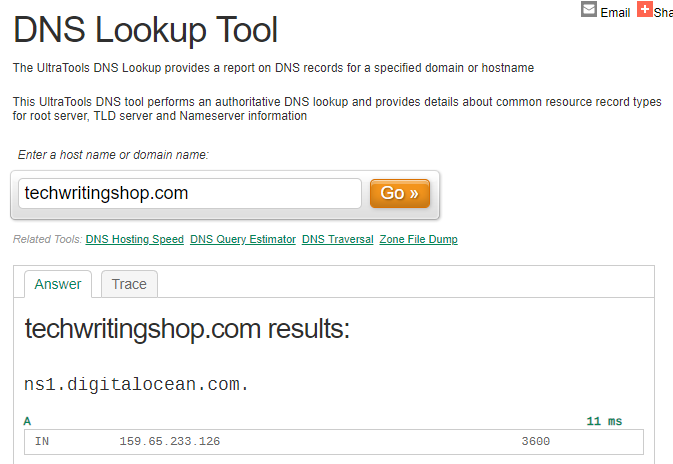
Setting up secondary DNS to keep your website up and running in the event your primary DNS provider goes down is easy with DNS Made Easy. We’re going to assume you... Read more
In recent articles, we’ve showed you 10 Useful Sudoers Configurations in Linux and Let Sudo Insult You When You Enter Incorrect Password, and in this article, we discovered a another... Read more
By Tim Brown Positioning itself as one of the most affordable Web hosting options on the market, iPage's hosting plans are cheap to get started with thanks to a big... Read more
I remember once reading that efficient system administrators are lazy people. The reason is not that they’re not doing their job or wasting their time – it is mostly because... Read more
Upgrading to Debian 8 (Jessie) Debian 8 (Jessie) is the most recent version of Debian, released in April 2015. This guide explains how to upgrade your system from Debian 7... Read more
Let us start by defining a bad sector/block, it’s a section on a disk drive or flash memory that can not be read from or written to anymore, as a... Read more
Computer networks have made it possible for end users to interact one with another in several ways. They have also provided a way to perform remote work without the hassle... Read more
