Today, we will guide you How to Install Snort on an Ubuntu 18.04 VPS or Dedicated Server.
How to Install Snort on an Ubuntu 18.04 VPS or Dedicated Server
Introduction
Intrusion detection systems are software that serves to monitor the network traffic for any suspicious activity and sends alerts or takes actions when discovered.
With the increasing sophistication of attacks, having firewalls and network perimeter security is not enough as we need to detect the threats before they cause a significant impact.
Some of the intrusion detection systems like Cisco’s IDS are unfortunately too expensive to purchase for some organizations.
Luckily Snort came to the rescue as being arguably one of the best open source intrusion detection systems in the market, running on almost all Linux, Unix, and Mac Os platforms.
Some of the features offered by Snort include:
- Network intrusion detection system
- Packet sniffer
- Packet logger
Prerequisites
- A VPS/Dedicated server running Ubuntu 18.04
- A non-root user with sudo privileges
Steps
Update system packages
$ sudo apt update && sudo apt upgrade
We will be installing a number of source files so you would want to create a folder to hold these packages.
$ mkdir snort_source_files && cd snort_source_files
Install Snort dependencies
Install the snort prerequisites in the created folder
$ sudo sudo apt install -y build-essential autotools-dev libdumbnet-dev libluajit-5.1-dev libpcap-dev / > libpcre3-dev zlib1g-dev pkg-config libhwloc-dev
Install cmake library
$ sudo apt install -y cmake
We will then want to install some optional but highly recommended libraries.
$ sudo apt install -y liblzma-dev openssl libssl-dev cpputest libsqlite3-dev uuid-dev
Since snort will be installed from Github, we definitely want to get the required tools to work with that.
$ apt install -y libtool git autoconf
Snort’s Data Acquisition Library has to have its dependencies installed:
$ sudo apt install -y bison flex
Install the Safe C library for buffer overflow prevention checks at runtime (caused by legacy C-library calls)
$ wget / >https://downloads.sourceforge.net/project/safeclib/libsafec-10052013.tar.gz $ tar -xzvf libsafec-10052013.tar.gz $ cd libsafec-10052013 $ ./configure $ make $ sudo make install
For performance optimization on high memory usage, we are going to install google performance tools (gfpertools):
$ cd ~/snort_source_files/ $ wget / >https://github.com/gperftools/gperftools/releases/download/gperftools-2.7/gperftools-2.7.tar.gz $ tar xzvf gperftools-2.7.tar.gz $ cd gperftools-2.7 $ ./configure $ make $ sudo make install
For faster pattern matching, we will install Ragel and Boost which are dependencies of Hyperscan that will assist us in faster multiple regex matching during scans.
Download and install Ragel library:
$ cd ~/snort_source_files/ $ wget http://www.colm.net/files/ragel/ragel-6.10.tar.gz $ tar -xzvf ragel-6.10.tar.gz $ cd ragel-6.10 $ ./configure $ make $ sudo make install
Download the Boost C++ libraries but do not install it.
$ cd ~/snort_source_files/ $ wget https://dl.bintray.com/boostorg/release/1.67.0/source/boost_1_67_0.tar.gz $ tar -xvzf boost_1_67_0.tar.gz
Download and install Hyper scan while referencing the location of the location of the boost headers source:
$ ~/snort_source_files/ $ wget https://github.com/intel/hyperscan/archive/v4.7.0.tar.gz $ tar -xvzf v4.7.0.tar.gz $ mkdir ~/snort_src/hyperscan-4.7.0-build $ cd hyperscan-4.7.0-build/ $ cmake -DCMAKE_INSTALL_PREFIX=/usr/local / >-DBOOST_ROOT=~/snort_source_files/boost_1_67_0/ ../hyperscan-4.7.0 $ make $ sudo make install
To test whether the hyper-scan works:
$ cd ~/snort_src/hyperscan-4.7.0-build/ $ ./bin/unit-hyperscan
We then need to install a memory serialization library called flatbuffers which is more efficient:
$ cd ~/snort_source_files $ wget https://github.com/google/flatbuffers/archive/v1.9.0.tar.gz -O flatbuffers-v1.9.0.tar.gz $ tar -xzvf flatbuffers-1.9.0.tar.gz $ mkdir flatbuffers-build && cd flatbuffers-build $ cmake ../flatbuffers-1.9.0 $ make $ sudo make install
Install Snort
We first need to install the Data Acquisition Library (DAQ) from snort’s website:
$ cd ~/snort_source_files $ wget https://www.snort.org/downloads/snortplus/daq-2.2.2.tar.gz $ tar -xzvf daq-2.2.2.tar.gz $ cd daq-2.2.2 $ ./configure $ make $ sudo make install
Update the shared libraries
$ sudo ldconfig
Finally, download snort source code and install it:
$ cd ~/snort_source_files $ git clone git://github.com/snortadmin/snort3.git $ cd snort3 $ ./configure_cmake.sh --prefix=/usr/local --enable-tcmalloc $ cd build $ make $ sudo make install
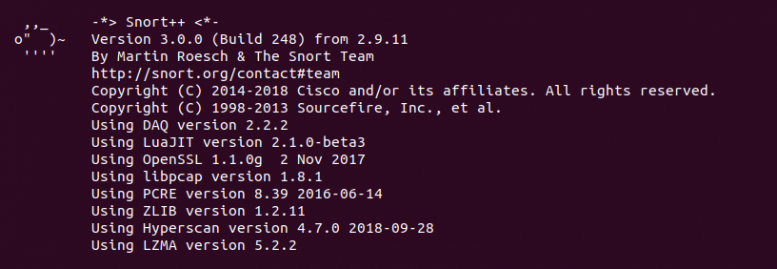
You can check whether snort has been installed:
$ /usr/local/bin/snort -V

Conclusion
If you have received the same output like the one above, it means you have successfully installed snort on your VPS/Dedicated host. The next step would be to permanently configure the global variables needed to run snort.