Snort is a popular choice for running a network intrusion detection systems or NIDS. It monitors the package data sent and received through a specific network interface. NIDS can catch threats targeting your system vulnerabilities using signature-based detection and protocol analysis technologies. NIDS software, when installed and configured appropriately, can identify the latest attacks, malware infections, compromised systems, and network policy violations. In this guide, you will find instructions on how to install Snort on CentOS 7. The install guide is also available for cloud servers running Debian 9 and Ubuntu 16.
How to install Snort on CentOS 7
Introduction
Intrusion detection systems are software that serves to monitor the network traffic for any suspicious activity and sends alerts or takes actions when discovered.
With the increasing sophistication of attacks, having firewalls and network perimeter security is not enough as we need to detect the threats before they cause a significant impact.
Some of the intrusion detection systems like Cisco’s IDS are unfortunately too expensive to purchase for some organizations.
Luckily Snort came to the rescue as being arguably one of the best open source intrusion detection systems in the market, running on almost all Linux, Unix, and Mac Os platforms.
Some of the features offered by Snort include:
- Network intrusion detection system
- Packet sniffer
- Packet logger
Prerequisites
- A VPS/Dedicated server running Centos 7
- A non-root user with sudo privileges
Steps to install Snort on CentOS 7
Step 1. Update system packages
sudo yum update -y
Setting up a basic configuration of Snort on CentOS is fairly simple but takes a few steps to complete. You will first need to install all the prerequisite software to ready your cloud server for installing Snort itself. Install the required libraries with the following command.
sudo yum install -y gcc flex bison zlib libpcap pcre libdnet tcpdump
The latest Snort version at this time also requires libnghttp2 which can be downloaded from the Extra Packages for Enterprise Linux (EPEL) and installed using the commands underneath.
sudo yum install -y https://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm sudo yum install -y libnghttp2
With the prerequisites fulfilled, next up is how to install Snort on CentOS 7. Snort can be installed with ready-built packages, which simplifies the setup process considerably, and allows you to install Snort easily with yum. Alternatively, you can download and install the Snort on CentOS manually from the source. Below you will find instructions for both of these methods.
Step 2. Install by Command-line interface
Option 1. Installing with yum
Snort provides convenient rpm packets for CentOS 7, which can be installed simply with the commands below. Snort itself uses something called Data Acquisition library (DAQ) to make abstract calls to packet capture libraries. Check the latest version number on the Snort front page, if a newer version of DAQ or Snort is available simply replace the version number in the following commands with the latest option.
sudo yum install https://www.snort.org/downloads/snort/daq-2.0.6-1.centos7.x86_64.rpm
sudo yum install https://www.snort.org/downloads/snort/snort-2.9.12-1.centos7.x86_64.rpm
And you are done with the installation, jump forward to the configuration to continue.
Option 2. Installing from the source
Setting up Snort on CentOS from the source code consists of a couple of steps: downloading the code, configuring it, compiling the code, installing it to an appropriate directory, and lastly configuring the detection rules.
Before getting started, you will also need the following development packages in addition to the already install prerequisites.
sudo yum install -y zlib-devel libpcap-devel pcre-devel libdnet-devel openssl-devel libnghttp2-devel luajit-devel
When ready, make a temporary download folder to your home directory and then change into it with the command below.
mkdir ~/snort_src && cd ~/snort_src
Download the latest DAQ source package from the Snort website with the wget command underneath. Replace the version number in the command if a newer source available.
wget https://www.snort.org/downloads/snort/daq-2.0.6.tar.gz
The download will only take a few seconds when complete extract the source code and jump into the new directory with the following commands.
tar -xvzf daq-2.0.6.tar.gz cd daq-2.0.6
Run the configuration script using its default values, then compile the program with make and finally install DAQ.
./configure && make && sudo make install
With the DAQ installed you can get started with Snort, change back to the download folder.
cd ~/snort_src
Next, download the Snort source code with wget. Check the latest version number from Snort website and replace it in the following command if necessary.
wget https://www.snort.org/downloads/snort/snort-2.9.12.tar.gz
Once the download is complete, extract the source and change into the new directory with these commands.
tar -xvzf snort-2.9.12.tar.gz cd snort-2.9.12
Then configure the installation with sourcefire enabled, run make and make install.
./configure --enable-sourcefire && make && sudo make install
With that done, continue below on how to set up the configuration files.
Step 3. Configuring Snort to run in NIDS mode
Next, you will need to setup Snort for your system. This includes editing some configuration files, downloading the rules that Snort will follow, and taking Snort for a test run.
Start with updating the shared libraries using the command underneath.
sudo ldconfig
Snort on CentOS gets installed to /usr/local/bin/snort directory, it is good practice to create a symbolic link to /usr/sbin/snort.
If you installed Snort with yum you can skip this command.
sudo ln -s /usr/local/bin/snort /usr/sbin/snort
Step 4. Setting up username and folder structure
To run Snort on CentOS safely without root access, you should create a new unprivileged user and a new user group for the daemon to run under.
sudo groupadd snort sudo useradd snort -r -s /sbin/nologin -c SNORT_IDS -g snort
Then create the folder structure to house the Snort configuration, just copy over the commands below. If you installed Snort using yum these directories should have already been added at install, but check to make sure.
sudo mkdir -p /etc/snort/rules sudo mkdir /var/log/snort sudo mkdir /usr/local/lib/snort_dynamicrules
Set the permissions for the new directories accordingly.
sudo chmod -R 5775 /etc/snort sudo chmod -R 5775 /var/log/snort sudo chmod -R 5775 /usr/local/lib/snort_dynamicrules sudo chown -R snort:snort /etc/snort sudo chown -R snort:snort /var/log/snort sudo chown -R snort:snort /usr/local/lib/snort_dynamicrules
Create new files for the white and blacklists as well as the local rules.
sudo touch /etc/snort/rules/white_list.rules sudo touch /etc/snort/rules/black_list.rules sudo touch /etc/snort/rules/local.rules
Then if you installed Snort from the source code, copy over the configuration files from the download folder.
Skip this if you installed Snort with yum.
sudo cp ~/snort_src/snort-2.9.12/etc/*.conf* /etc/snort sudo cp ~/snort_src/snort-2.9.12/etc/*.map /etc/snort
Next up, you will need to download the detection rules Snort will follow to identify potential threats. Snort provides three tiers of rule sets, community, registered and subscriber rules.
- Community rules are freely available though slightly limited.
- By registering for free on their website you get access to your Oink code, which lets you download the registered users rule sets.
- Lastly, subscriber rules are just that, available to users with an active subscription to Snort services.
Underneath you can find instructions for downloading both community rules or registered user rule sets.
Option 1. Using community rules
If you just want to quickly test out Snort, grab the community rules using wget with the command below.
wget https://www.snort.org/rules/community -O ~/community.tar.gz
Extract the rules and copy them to your configuration folder.
sudo tar -xvf ~/community.tar.gz -C ~/
sudo cp ~/community-rules/* /etc/snort/rules
By default, Snort on CentOS expects to find a number of different rule files which are not included in the community rules. Comment out the unnecessary lines using the next command.
sudo sed -i 's/include \$RULE\_PATH/#include \$RULE\_PATH/' /etc/snort/snort.conf
Option 2. Obtaining registered user rules
You can also take a moment and register on the Snort website. Registering gives you access to use their Oink code to download the registered user rules. You can find the code in the Snort user account details.
Replace the oinkcode in the following command with your personal code.
wget https://www.snort.org/rules/snortrules-snapshot-29120.tar.gz?oinkcode=oinkcode -O ~/registered.tar.gz
Once downloaded, extract the rules and copy them over to your configuration directory.
sudo tar -xvf ~/registered.tar.gz -C /etc/snort
The rule sets for the registered users include an extensive amount of useful preconfigured detection rules. If you tried out Snort with the community rules first, you can enable additional rules by uncommenting their inclusions towards the end of the snort.conf file.
Step 5. Configuring the network and rule sets
With the configuration and rule files in place, edit the snort.conf to modify a few parameters. Open the configuration file for editing with the following command.
sudo vi /etc/snort/snort.conf
Find these sections shown below in the configuration file and change the parameters to reflect the examples here.
# Setup the network addresses you are protecting ipvar HOME_NET server_public_ip/32
# Set up the external network addresses. Leave as "any" in most situations ipvar EXTERNAL_NET !$HOME_NET
# Path to your rules files (this can be a relative path) var RULE_PATH /etc/snort/rules var SO_RULE_PATH /etc/snort/so_rules var PREPROC_RULE_PATH /etc/snort/preproc_rules
# Set the absolute path appropriately var WHITE_LIST_PATH /etc/snort/rules var BLACK_LIST_PATH /etc/snort/rules
In the same snort.conf file, scroll down to the section 6 and set the output for unified2 to log under filename of snort.log like below.
# unified2 # Recommended for most installs output unified2: filename snort.log, limit 128
Lastly, scroll down towards the bottom of the file to find the list of included rule sets. You will need to uncomment the local.
rules to allow Snort to load any custom rules.
include $RULE_PATH/local.rules
If you are using the community rules, add the line underneath to your ruleset as well, for example just below your local.rules line.
include $RULE_PATH/community.rules
Once you are done with the configuration file, save the changes and exit the editor
Step 6. Validating settings
Your Snort should now be ready to run. Test the configuration using the parameter -T to enable test mode and validate the configuration.
sudo snort -T -c /etc/snort/snort.conf
If you get an error while loading shared libdnet.1 libraries, create the following link and try again.
ln -s /usr/lib64/libdnet.so.1.0.1 /usr/lib64/libdnet.1
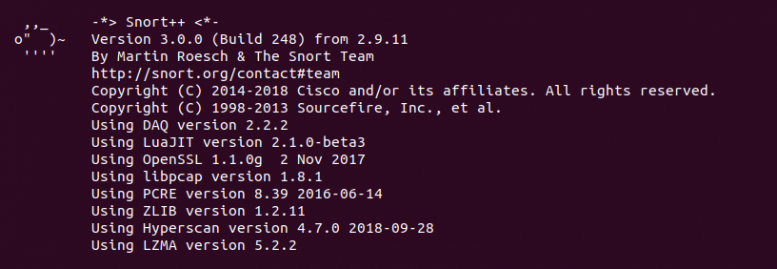
After running the Snort configuration test,
you should get a message like this example below.
--== Initialization Complete ==--
,,_ -*> Snort! <*-
o" )~ Version 2.9.12 GRE (Build 325)
'''' By Martin Roesch & The Snort Team: http://www.snort.org/contact#team
Copyright (C) 2014-2018 Cisco and/or its affiliates. All rights reserved.
Copyright (C) 1998-2013 Sourcefire, Inc., et al.
Using libpcap version 1.5.3
Using PCRE version: 8.32 2012-11-30
Using ZLIB version: 1.2.7
Rules Engine: SF_SNORT_DETECTION_ENGINE Version 3.0
Preprocessor Object: appid Version 1.1
Preprocessor Object: SF_DNP3 Version 1.1
Preprocessor Object: SF_MODBUS Version 1.1
Preprocessor Object: SF_GTP Version 1.1
Preprocessor Object: SF_REPUTATION Version 1.1
Preprocessor Object: SF_SIP Version 1.1
Preprocessor Object: SF_SDF Version 1.1
Preprocessor Object: SF_DCERPC2 Version 1.0
Preprocessor Object: SF_SSLPP Version 1.1
Preprocessor Object: SF_DNS Version 1.1
Preprocessor Object: SF_SSH Version 1.1
Preprocessor Object: SF_SMTP Version 1.1
Preprocessor Object: SF_IMAP Version 1.0
Preprocessor Object: SF_POP Version 1.0
Preprocessor Object: SF_FTPTELNET Version 1.2
Snort successfully validated the configuration!
Snort exiting
In case you get an error, the print out should tell you what the problem was and where to fix it. Most likely problems are missing files or folders, which you can usually resolve by either adding any you might have missed in the setup above, or by commenting out unnecessary inclusion lines in the snort.conf file. Check the configuration part and try again.
Step 7. Testing the configuration
To test if Snort is logging alerts as intended, add a custom detection rule alert on incoming ICMP connections to the local.rules file. Open your local rules in a text editor.
sudo vi /etc/snort/rules/local.rules
Then add the following line to the file.
alert icmp any any -> $HOME_NET any (msg:"ICMP test"; sid:10000001; rev:001;)
The rule consists of the following parts:
- action for traffic matching the rule, alert in this case
- traffic protocol like TCP, UDP or ICMP like here
- the source address and port, simply marked as any to include all addresses and ports
- the destination address and port, $HOME_NET as declared in the configuration and any for port
- some additional bits
- log message
- unique rule identifier (sid) which for local rules needs to be 1000001 or higher
- rule version number.
Save the local.rules and exit the editor. You then need to restart Snort since you made changes to the files it loads.
Start Snort with -A console options to print the alerts to stdout. You will need to select the correct network interface with the public IP address of your server, for example, eth0.
sudo snort -A console -i eth0 -u snort -g snort -c /etc/snort/snort.conf
If you are not sure which interface to use, check your UpCloud control panel for the public IPv4 address of your server in the Network settings. You can also use the following command on your server.
ip addr
The output will list all of your currently configured network interfaces. Find the one with the same public IP address as shown in the Network settings, commonly eth0.
With Snort up and running ping your cloud server from any other computer. You should see a notice for each ICMP call in the terminal running Snort.
07/12-11:20:33.501624 [**] [1:10000001:1] ICMP test [**] [Priority: 0] {ICMP} 83.136.252.118 -> 80.69.173.202
After the alerts show up you can stop Snort with ctrl+C.
Snort records the alerts to a log under /var/log/snort/snort.log.timestamp, where the time stamp is the point in time when Snort was started marked in Unix time. You can read the logs with the command underneath. Since you have only run Snort once, there is only one log, complete your command by pressing TAB.
snort -r /var/log/snort/snort.log.
The log shows a warning for each ICMP call with source and destination IPs, time and date, plus some additional info as shown in the example below.
WARNING: No preprocessors configured for policy 0. 07/12-11:20:33.501624 83.136.252.118 -> 80.69.173.202 ICMP TTL:63 TOS:0x0 ID:20187 IpLen:20 DgmLen:84 DF Type:8 Code:0 ID:13891 Seq:1 ECHO
Step 8. Running Snort in the background
Lastly, if you wish to run Snort on CentOS as a service in the background you should download a startup script from Snort documentation.
If you installed Snort using yum, you should already have the startup script configured. Start the service as described below.
Use the following commands to get and install a startup script for your system.
wget https://www.snort.org/documents/snort-startup-script-for-centos -O ~/snortd sudo chmod 755 ~/snortd && sudo mv ~/snortd /etc/init.d/
Next, reload the system daemon.
sudo systemctl daemon-reload
Then start the service.
sudo systemctl start snortd
The startup script also includes the other usual systemctl commands: stop, restart, and status. For example, you can check the status of the service with the following command.
sudo systemctl status snortd
Conclusions
Congratulations, you should have now successfully configured and tested a network-based intrusion detection system. This guide however only covers the very basics with an introduction to Snort and NIDS in general. To get more out of your installation, check out the deployment guides over at the Snort documents page, or jump right into writing your own detection rules with their helpful Snort rules info graph.
Source: Internet