PHP code can be integrated into your Web pages together with HTML code. When your Web server receives a query for a page, the page is primarily offered to the PHP handler. The PHP handler will output HTML code without adjusting it and carries out any PHP command. It also outputs any HTML code created by the PHP command.
This produces a Web page with contents that are altered on the server prior to the time they are transferred to the requestor.
These abilities of PHP also make it prone to security risk due to the fact that it allows active collection of data, reception of data and processing of data from any location on the World Wide Web or the internet. Hackers may try to post malicious data and scripts and hoax your server into collecting and running malicious scripts as your own.
The unscrupulous elements may as well try to read and write files on your server to overtake the Website and utilize it to carry out their hideous acts.
The good news is that you can actually adjust your PHP settings to boost the security of a PHP installation and assist to keep the Website safe from any form of vicious attacks.
The Php.ini file stipulates the configuration settings PHP utilizes when it runs on your Website. The Php.ini file stipulates, the things PHP scripts are permitted to do and what they are prevented from doing.
Below are recommended settings that determine the security of your PHP configuration setting.
Step 1: Configure The Following Recommended Php.ini settings:
1. allow_url_fopen=Off allow_url_include=Off
consoleCopy
allow_url_fopen = Off
This setting disables isolated URLs. This may make files that handle functions vulnerable to code injections. This setting is very significant due to the fact that it inhibits URLs from being utilized in statements like include (). Configure”allow_url_fopen to “Off,” implies that only files on your Website can be integrated.
That means you cannot integrate any file from a different server. It also means that no attacker can be able to do that through Remote File Inclusion (RFI) attacks. (In an RFI attack, san imposter integrates a URL in an HTTP query with the view that it will deceive your script into thinking it is being run by yours. A command like integrate- (“http://website.com/page.php”), for instance, would not be executed. Incorporate a file from your own site by spelling out its path and filename.
2. register_globals=Off Disable Register_globals Setting
consoleCopy
register_globals = Off
For instance, for the URL http://site.com/index.php?variable=***value***, the variable moves into your script with its value set to value when register_globals is “On.” When register_globals is “Off,” nevertheless, variables do not by routine get transferred into the variable list of your script’s variable list. This makes it harder for hackers to infuse code into your script.
3. open_basedir=”c:inetpub”
This script setting is used for limiting where PHP systems can read and write on a file system.
4. safe_mode=Off safe_mode_gid=Off
This setting is utilized to disable safe mode.
consoleCopy
safe_mode = Off
This setting is not in the “recommended Php.ini” file. It limits the permissions granted to the PHP scripts to run. Many third-party scripts do not function rightly when the safe_mode is enabled and set to “On.” Notice that the starting with PHP 6 safe_mode is not in existence.
5. max_execution_time=30 max_input_time=60
This setting restricts the time it takes to execute script
6. memory_limit=16M upload_max_filesize=2M post_max_size=8M max_input_nesting_levels=64
This setting restricts the memory and size of files that can be used.
7. display_errors=Off log_errors=On error_log=”C:pathofyourchoice”
This setting helps to configure error messages and logging.
consoleCopy
DISPLAY_ERRORS =Off display_startup_errors = Off log_errors = On error_reporting = E_ALL
These commands stipulate that the entire errors and warnings are logged to your error log text file and spell out that none of the errors or warnings are displayed on any Web page that is transferred outside your server.
Errors ought not to be displayed in public due to the fact that they can assist someone to determine the way they want to launch an attack on your server. You need to constantly verify your error log anytime you are testing a fresh code.
8. fastcgi.logging=0
Internet Information Services (IIS) FastCGI module will not return the query when PHP transfers any information on stderr by utilizing FastCGI protocol. By disabling FastCGI logging, you’ll stop PHP from transferring error message across to the stderr, and creating 500 answer codes for the user.
9. expose_php=Off
This setting is utilized to conceal that PHP is integrated in to the web server.
10. $_SERVER[‘DOCUMENT_ROOT’]
consoleCopy
include($_SERVER['DOCUMENT_ROOT'] . '/page.php');
$_SERVER[‘DOCUMENT_ROOT’] is a superglobal variable that is configured to serve as the root folder of your website. (Observe that there is no trailing “/”; you need to offer a leading “/” in ‘/page.php’.)
If you intend to incorporate a static content from a different website you own like integrate (‘http://myothersite.com/includes/footer.php’), get a duplicate of the content in the present site and after that integrate it locally.
If you really need to integrate content from an isolated site, you should always make use of URLs and set allow_url_fopen = On. You’ll, however, implement another security option to be safe from RFI attacks.
11. error_log = /home/yourUserID/public_html/phperr.txt
consoleCopy
error_log = /home/yourUserID/public_html/phperr.txt
This setting determines the path and file that your PHP errors and cautions are logged in to. You ought to utilize a text file for error logging. However, you need to be aware that the text file will build up errors forever till such a time you clear it. Save the error log file in a position on your Website that cannot be accessed by the general public.
12. expose_php = Off
consoleCopy
expose_php = Off
This setting lets the headers that follow the departing pages conceal that you are running PHP or related version.
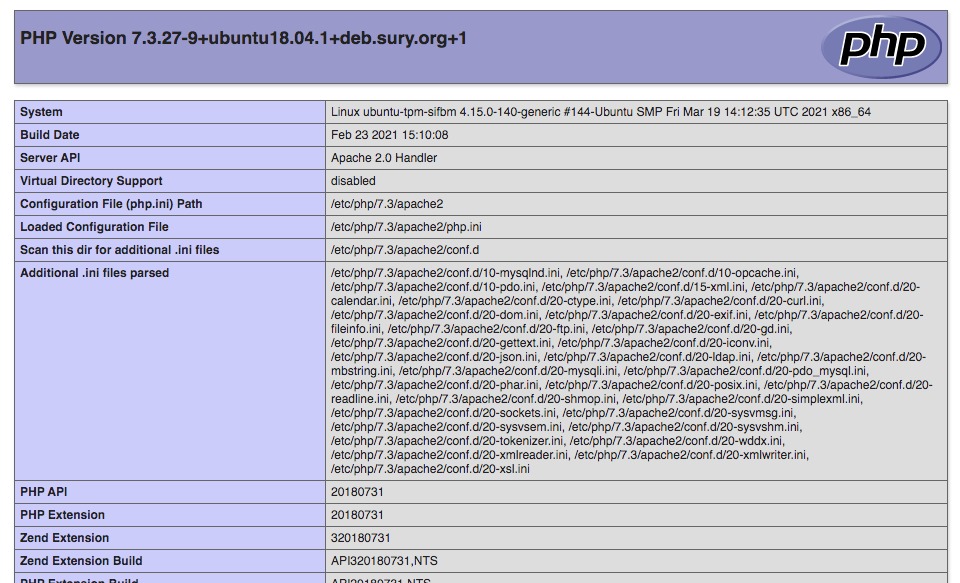
STEP 2: View the PHP Settings
After configuring the above PHP settings, you can check your settings to get the complete report about all your PHP settings. To do this, follow the steps below:
1. Generate a text file with a .php extension:
XMLCopy <?php phpinfo(); ?>
2. Upload it to your server and if possible into a folder that is password-protected.
3. Click to open your Web browser, and key in the address into the address bar:
consoleCopy
http://yoursite.com/whatever/filename.php
4. Type your username and password to gain access into the protected folder and check the resultant page.
5. Click Save to save the resultant page in your local computer. You can as well print it for future reference.
6. Click Delete to delete the .php file out of your server.
Check out these top 3 Windows hosting services:
0