Brief Description
FTP is usually insecure exposing clear-text passwords, usernames and files to hackers. Very Secure FTP Daemon (VSFTPD) is adopted to secure these transfers using SSL-TLS to Centos 7 FTP Server.
This short tutorial is highly important for Intermediate Level System Administrators and Users who usually transfer highly confidential data (documents, images, e.t.c) to their company’s or organization’s FTP servers from Windows PCs using FileZilla.
Special note: consult HostAdvice’s Best Linux hosting services page to find the leading web hosts in this category, including expert and user reviews.
Installation
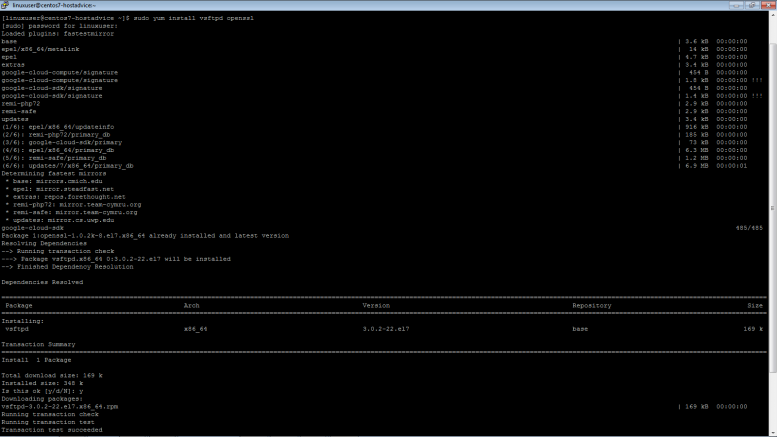
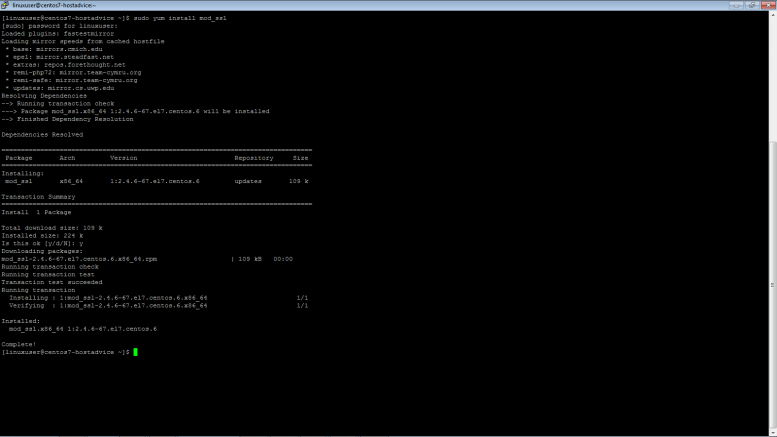
Install vsftpd and openssl packages on the Centos 7 Linux server
$ sudo yum install vsftpd openssl mod_ss
Switch to root user and enter root password
FTP data is usually insecure since information (usernames, passwords, commands, data) is transmitted unencrypted in clear text. Therefore it’s very IMPORTANT to encrypt the FTP connection using SSL/TLS.
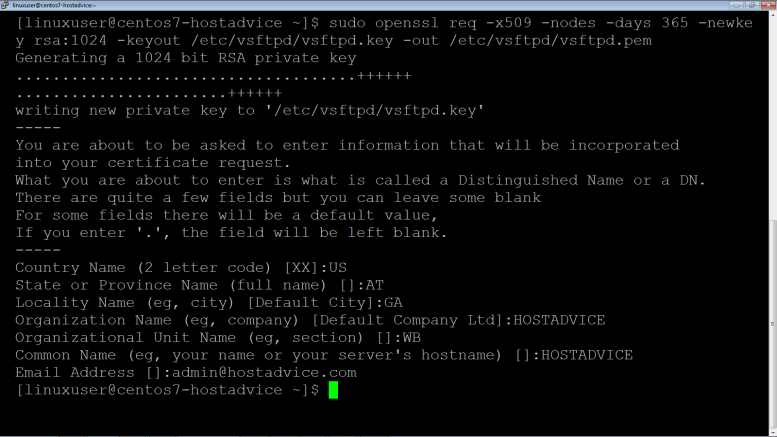
Generate a self-signed certificate to secure the FTP server connections.
$ sudo openssl req -x509 -nodes -days 365 -newkey rsa:2048 –keyout /etc/vsftpd/vsftpd.key -out /etc/vsftpd/vsftpd.pem
Configuration
Edit the configuration file /etc/vsftpd/vsftpd.conf
$ sudo vim /etc/vsftpd/vsftpd.conf
Ensure configurations as shown below:
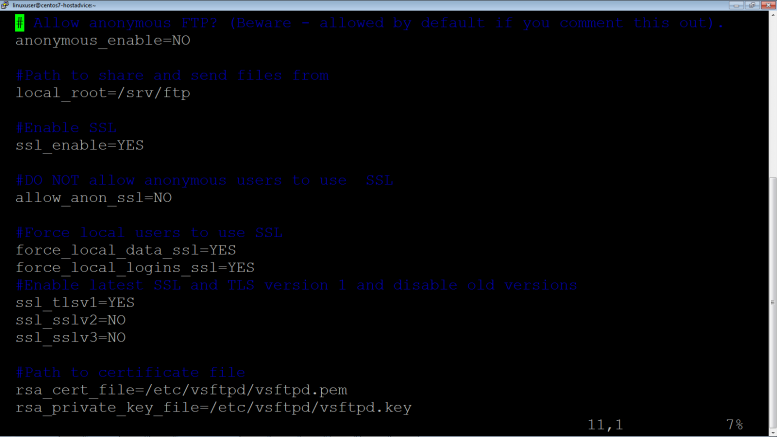
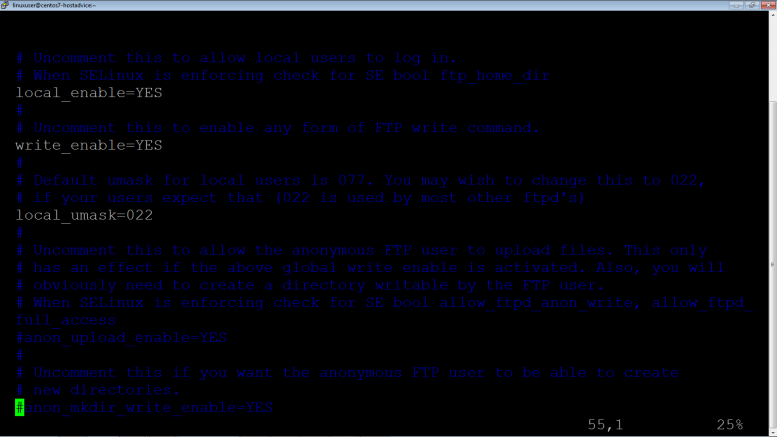
# Allow anonymous FTP? (Beware - allowed by default if you comment this out). anonymous_enable=NO #Path to share and send files from local_root=/srv/ftp #Enable SSL ssl_enable=YES #DO NOT allow anonymous users to use SSL allow_anon_ssl=NO #Force local users to use SSL force_local_data_ssl=YES force_local_logins_ssl=YES #Enable latest SSL and TLS version 1 and disable old versions ssl_tlsv1=YES ssl_sslv2=NO ssl_sslv3=NO #Path to certificate file rsa_cert_file=/etc/vsftpd/vsftpd.pem rsa_private_key_file=/etc/vsftpd/vsftpd.key # Uncomment this to allow local users to log in. # When SELinux is enforcing check for SE bool ftp_home_dir local_enable=YES # # Uncomment this to enable any form of FTP write command. write_enable=YES
Configure Firewall
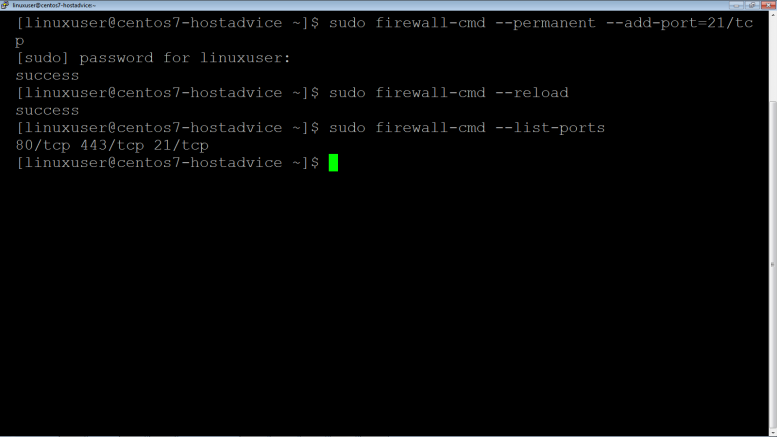
Enable vsftpd connections via firewall-cmd
$ sudo firewall-cmd --permanent --add-service=ftp
OR
$ sudo firewall-cmd --permanent --add-port=21/ftp $ sudo firewall-cmd –reload
Special Note: Vsftpd also uses ssh port i.e. 22 so ensure firewall-cmd allows for ssh connections
Add FTP User
Create the ftp root directory
$ sudo mkdir –p /srv/ftp
Switch to root user and enter root password
$ su –
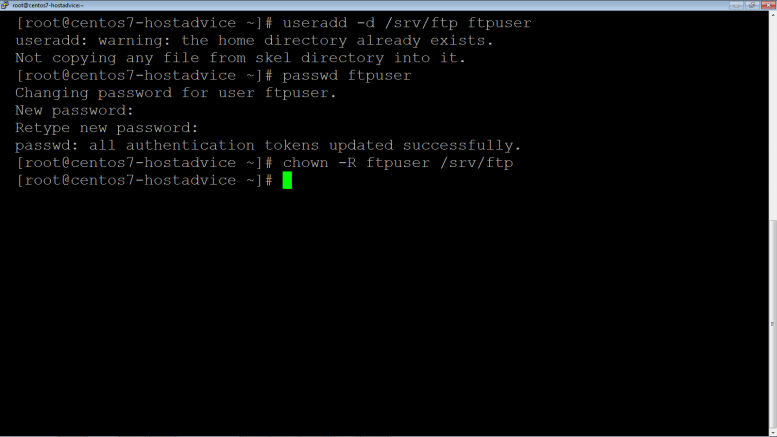
As root, create user that’s allowed to login into the ftp directory
# useradd –d /srv/ftp/ ftpuser
-d Set /srv/ftp as the home directory for ftpuser
Set the password for the ftpuser
# passwd ftpuser
Set the ftp root directory to be owned by ftpuser
# chown –R ftpuser /srv/ftp
Switch back from root user
# su - linuxuser
Start the VSFTPD service
$ sudo systemctl start vsftpd
Confirm VSFTPD service is running
$ sudo systemctl status
Conduct FTP Login Test
Login from Windows Client Machine using FileZilla
If you try to login the default way without SSL, it will fail to login and produce an error as shown below:
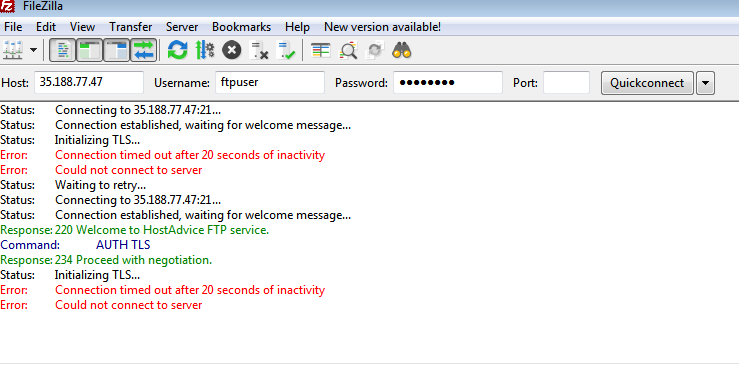
Now try accessing using SSL as shown below:
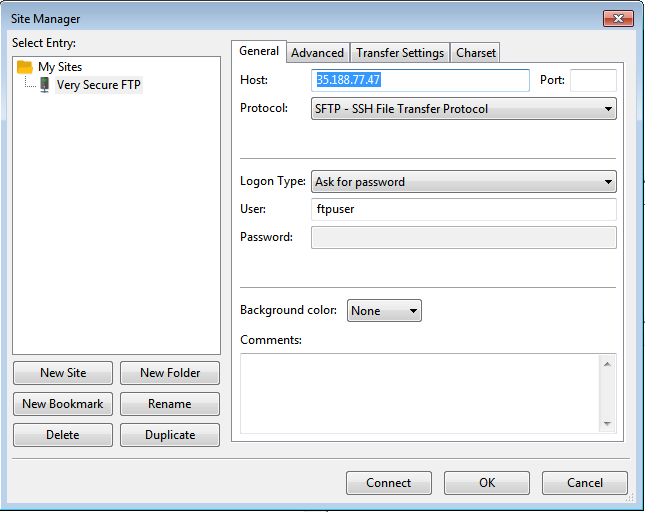
Go to File > Site Manager
Click “New Site” and name it “Very Secure FTP”
While on General Tab:
Host: Enter the public ip address or domain name or hostname
Protocol: Select “SFTP – Secure Shell File Transfer Protocol”
Logon Type: Select “Ask for Password”
Enter the username and password for ftp user.
Finally click on “Connect”
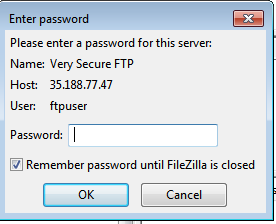
Enter password upon prompt:
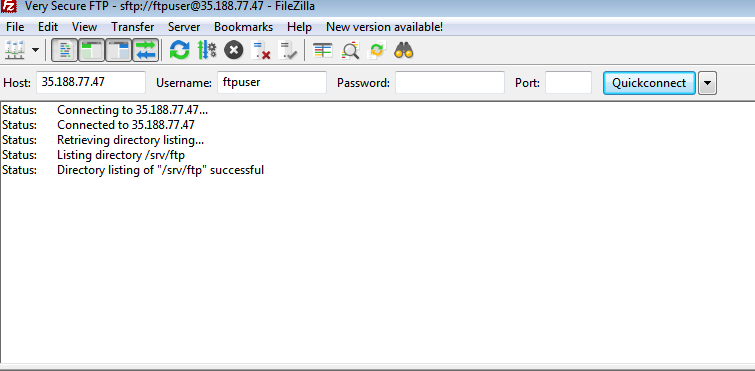
Note the successful connection.
Special Note: Please note this will work ONLY IF either of the following are done:
Password Authentication is enabled in /etc/ssh/sshd_config/
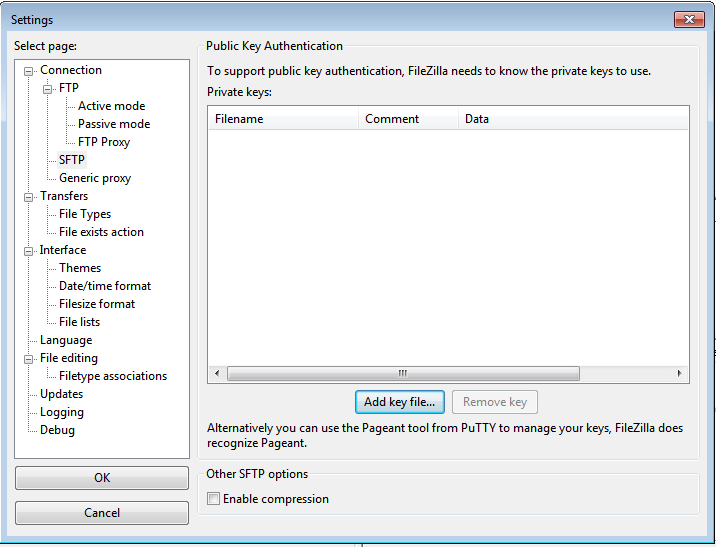
If Password Authentication is disabled and only SSH Keys Private Authentication is enabled, you have to configure Filezilla ssh keys private key authentication with the Linux Server. ilezilla-Edit-Go to Edit > Settings
Select SFTP > Add Key File.
Then choose the private key that you;ve used to authenticate with the public key in the Linux Server.
Check out the top 3 Linux hosting services
0