How To Set up a VSFTPD Server on an Ubuntu
Brief Description
FTP data is usually insecure since information (usernames, passwords, data) is transmitted unencrypted in clear-text. It’s very IMPORTANT to encrypt the FTP connections to Linux FTP Servers using VSFTPD (SSL/TLS).
This short tutorial is highly important for Intermediate Level System Administrators and Users who usually transfer highly confidential data (documents, images, e.t.c) to their company’s or organization’s Linux FTP servers.
Special note: consult HowVPS‘s Best Linux hosting services page to find the leading web hosts in this category, including expert and user reviews.
Step 1: Installation
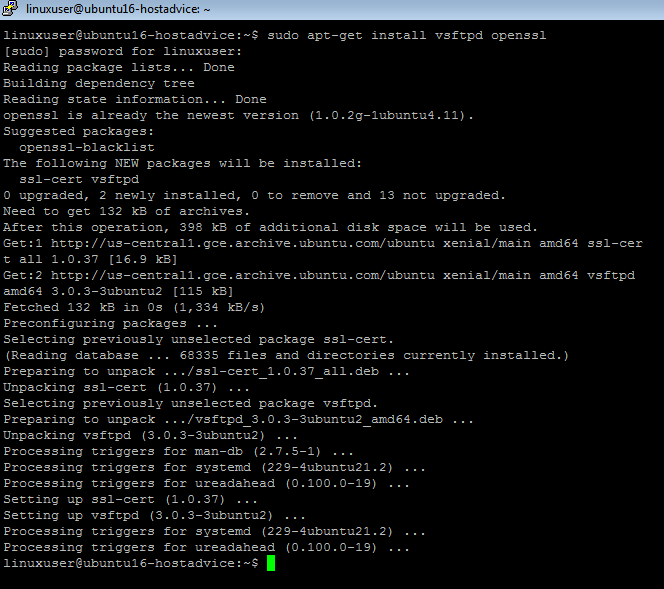
Install vsftpd and openssl packages on the Ubuntu 16.04 Linux server
$ sudo apt-get install vsftpd openssl
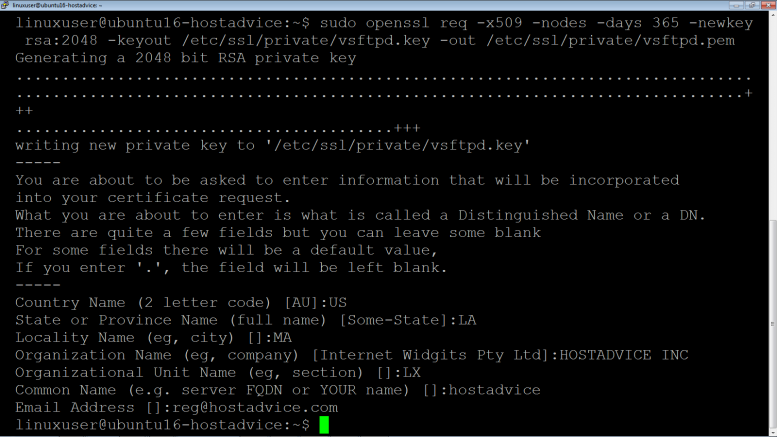
Generate a self-signed certificate to secure the FTP server connections.
$ sudo openssl req -x509 -nodes -days 365 -newkey rsa:2048 –keyout /etc/ssl/private/vsftpd.key -out /etc/ssl/private/vsftpd.pem
Step 2: Configuration
Edit the configuration file /etc/vsftpd.conf
$ sudo cp /etc/vsftpd.conf /etc/vsftpd.conf.bak $ sudo vim /etc/vsftpd.conf
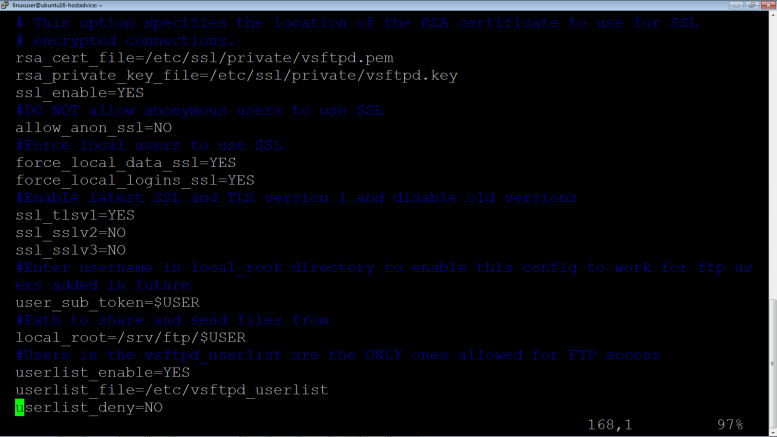
Ensure configurations as shown below:
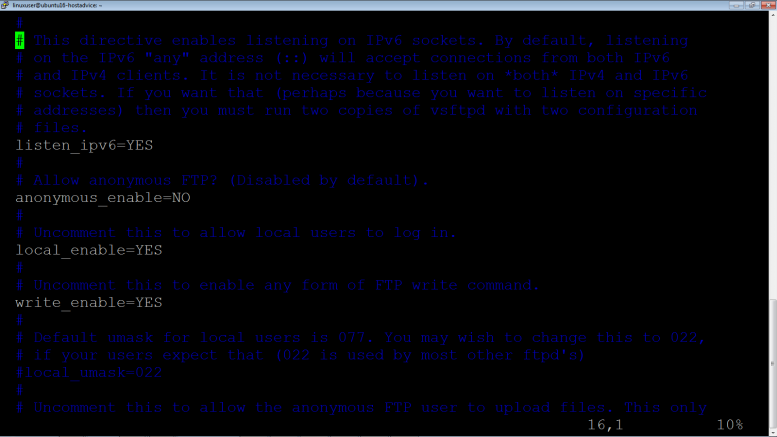
# Allow anonymous FTP? (Disabled by default). anonymous_enable=NO # # Uncomment this to allow local users to log in. local_enable=YES # # Uncomment this to enable any form of FTP write command. write_enable=YES
# This option specifies the location of the RSA certificate to use for SSL # encrypted connections. rsa_cert_file=/etc/ssl/private/vsftpd.pem rsa_private_key_file=/etc/ssl/private/vsftpd.key ssl_enable=YES #DO NOT allow anonymous users to use SSL allow_anon_ssl=NO #Force local users to use SSL force_local_data_ssl=YES force_local_logins_ssl=YES #Enable latest SSL and TLS version 1 and disable old versions ssl_tlsv1=YES ssl_sslv2=NO ssl_sslv3=NO #Enter username in local_root directory to enable this config to work for ftp users added in future user_sub_token=$USER #Path to share and send files from local_root=/srv/ftp/$USER #Users in the vsftpd_userlist are the ONLY ones allowed for FTP access userlist_enable=YES userlist_file=/etc/vsftpd_userlist userlist_deny=NO
Start vsftpd service
$ sudo systemctl start vsftpd $ sudo systemctl status vsftpd
Step 3: Configure Uncomplicated Firewall (UFW)
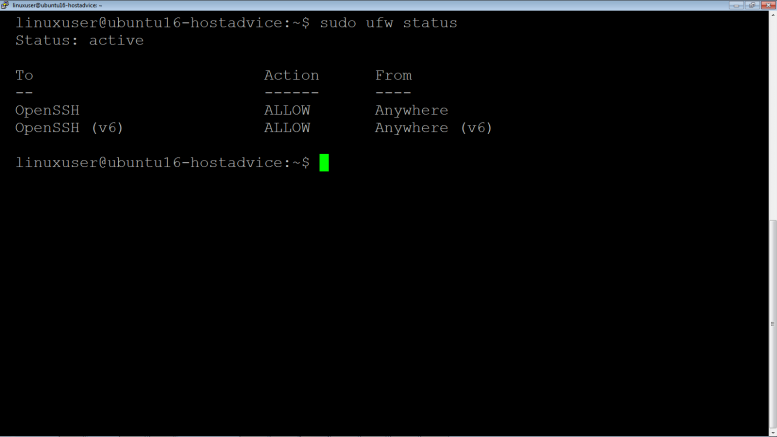
Enable vsftpd connections via ufw
$ sudo ufw status
Special Note: By-default, ufw is usually installed in Ubuntu, however if for some reasons it’s not there you can install using
$ sudo apt-get install ufw
Ensure the firewall allows FTP connections
$ sudo ufw allow 20/tcp $ sudo ufw allow 21/tcp $ sudo ufw status
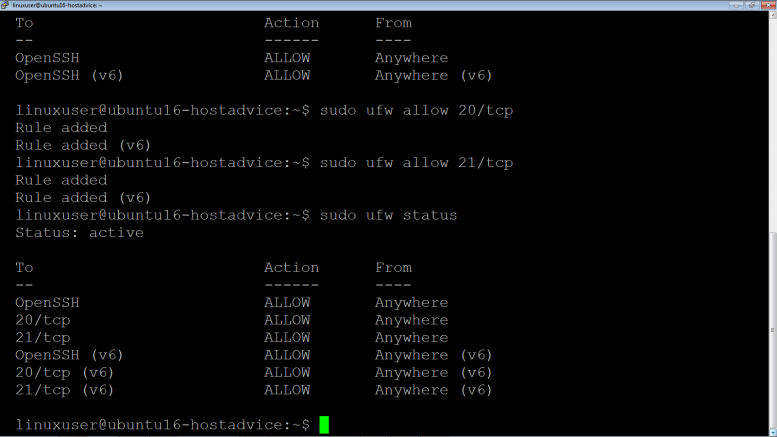
Special Note: Vsftpd also uses ssh port i.e. 22 so ensure ufw allows for ssh connections
Step 4: Add FTP User
Switch to root user and enter root password
$ su –
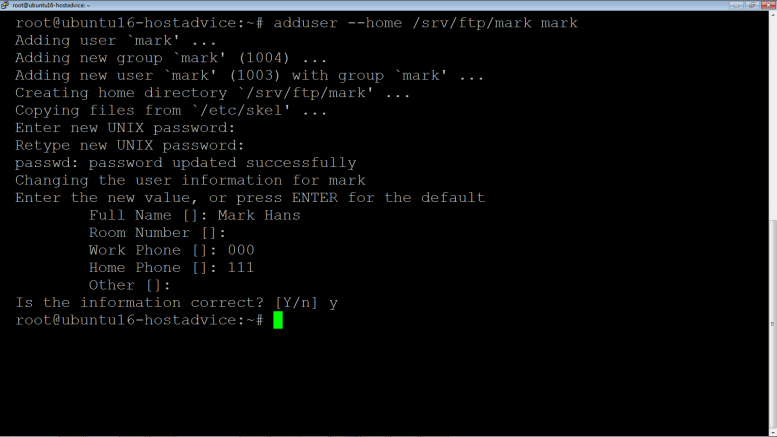
As root, create user that’s allowed to login into mark’s ftp directory
# adduser --home /srv/ftp/mark mark
-d Set /srv/ftp/mark as the home directory for ftpuser
Set the ftp root directory to be owned by ftpuser
# chown –R mark /srv/ftp/mark
Switch back from root user
# su - linuxuser
Include mark in /etc/vsftpd_userlist to be allowed ftp access
# sudo vim /etc/vsftpd_userlist
Then enter “mark” to the file.
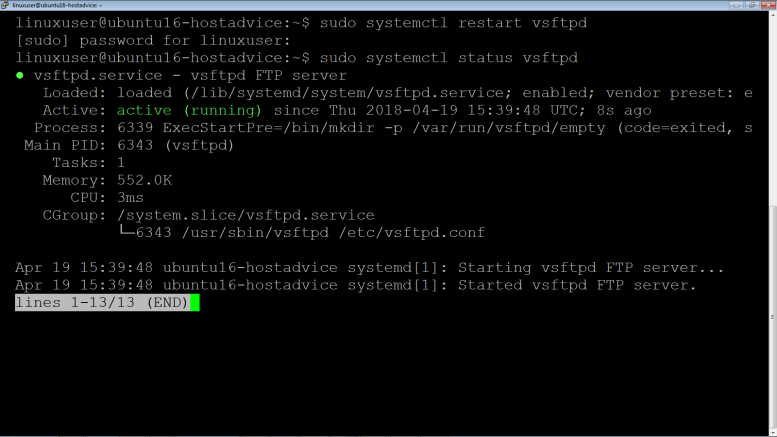
Start the VSFTPD service
$ sudo systemctl restart vsftpd
Confirm VSFTPD service is running
$ sudo systemctl status vsftpd
Step 5: Conduct FTP Login Test
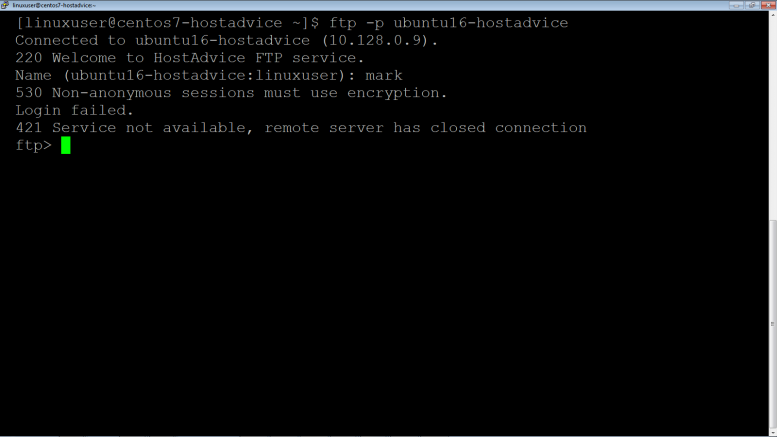
Login from a Linux Local Machine
$ ftp -p ubuntu16-hostadvice
If you try to login the default way without SSL, it will fail to login and produce an error as shown below:
Now try accessing using SSL i.e SFTP (Secure FTP) Protocol as shown below:
$ sftp mark@ubuntu16-hostadvice
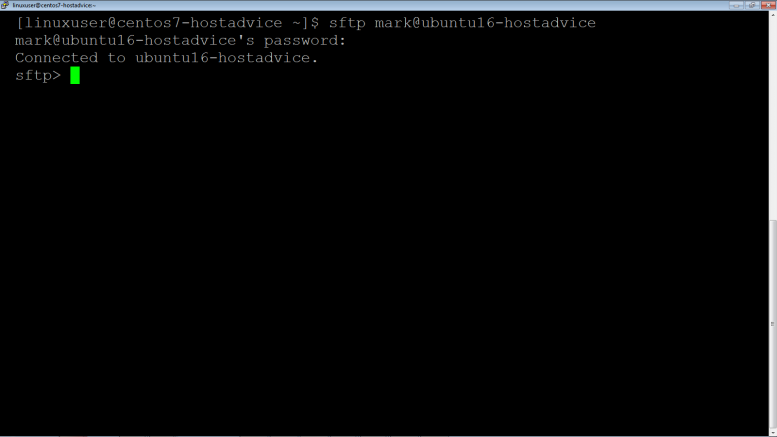
Note the successful connection.
Special Note: Please note this will work ONLY IF either of the following are done:
Password Authentication is enabled in /etc/ssh/sshd_config/
If Password Authentication is disabled and only SSH Keys Private Authentication is enabled, you have to configure ssh keys private key authentication for that specific ftp user with the Linux Server.