mod_evasive is a module for Apache that automatically takes action when an HTTP DoS attack or brute force attack is detected. It is used to make logs and alert for issues.
This module creates a list of URLs and IP addresses and the users who fall in the condition set in the configuration, these users will receive a 403 error. In this guide, you will learn how you can enable this feature for CentOS, Ubuntu, Debian.
Prerequisites
- Apache server
- Text editor
Step 1:
To install the mod_evasive module you will need the httpd-devel package. It contains the file needed to build Dynamic Shared Objects for Apache. Run the following command to install httpd-devel package.
yum install httpd-devel
Used for CentOS
apt-get install apache2-utils
This command is used for Ubuntu & Debian
Step 2:
Download the mod_evasive module using the wget command in your terminal
cd /usr/src wget http://www.zdziarski.com/blog/wp-content/uploads/2010/02/mod_evasive_1.10.1.tar.gz
Extract the downloaded module
tarxzfmod_evasive*.tar.gz
Now, go inside the extracted foler.
cd mod_evasive
Step 3:
Now you need to install a tool called apxs2. It is used along with Apache for building and installing added functionality.
apxs2-ciamod_evasive20.c
This command will not run if httpd-devel is not installed properly.
Step 4:
Download and install the epel repository to move ahead.
yum install epel-release
After the installation of the epel repository, install mod_evasive using
yum install mod_evasive
Step 5:
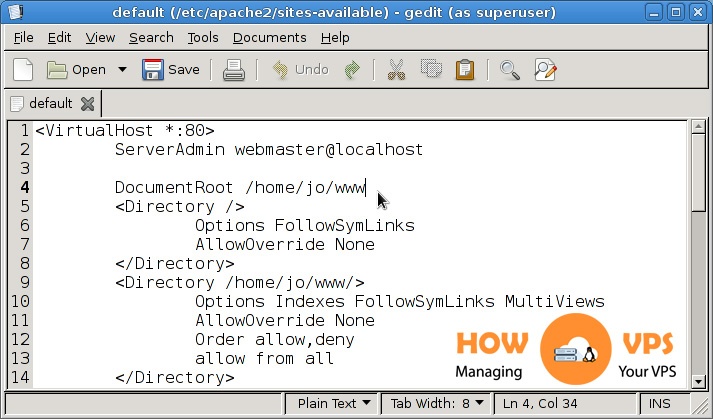
You can now verify if the module has been added to the Apache functionality or not. Open your configuration file to check if the module has been added or not.
The configuration file is located at a different location for a different operating system.
For Ubuntu/Debian,
/etc/apache2/apache2.conf
For CentOS,
/etc/httpd/conf/httpd.conf
In Ubuntu, add the following line at the end of the config file
LoadModule evasive20_module /usr/lib/httpd/modules/mod_evasive20.so
For CentOS, Search for Include and look for
Include mods-enabled/*.conf
Add the above lines for each Operating system if they are not available in the config file.
Step 6:
To set the rule for DOS count and DOS interval and other settings, add the following code to the same config file from Step 5.
<IfModulemod_evasive20.c> DOSHashTableSize 4012 DOSPageCount 3 DOSSiteCount 50 DOSPageInterval 1 DOSSiteInterval 1 DOSBlockingPeriod 70 DOSEmailNotify <test@example.com> </IfModule>
This config will send an alert to the mentioned email address if the DOS attack meets the above set configuration.
Step 7:
Once the configuration has been set, you can now restart the Apache web server for the changes to be reflected.
service httpd restart
Also, make sure the module is loaded into Apache in the next reboot by using the following command.
httpd -M | grep evasive

Conclusion:
That’s it. You have now successfully installed the mod_evasive module in Apache and your app is safer now.