If you are running IIS, you may be considering what steps you need to take to secure your web server.
This is important because while IIS does come with a number of security features, they do take some configuration before you can take advantage of them. In this article, we’re going to go over some simple steps to secure your IIS installations.
Transfer The Inetpub Folder To Another Drive
By default, lt the Inetpub folder is where your web content is located. Newer versions of IIS put this folder on the system drive but it’s best to move the folder to a different partition.
Separating the content folder from the operating system is good practice from a security standpoint and it makes it easier to back up your data.
Set Up Suitable IIS Modules
Part of securing IIS is making sure you’re only running the modules that you need. IIS comes with over 30 and running extra services that you don’t need increases the chance someone will find a security vulnerability to exploit.
Removing modules you don’t need is one of the simplest ways to increase the security of your IIS server. The steps below will walk you through how to check which modules are installed and how to remove them:
- Navigate to the IIS Manager and open it
- Click on the engine name to examine all the elements that come with it. Alternatively, navigate to the particular website to examine all the modules allowed for that particular site.
- Click on ‘Modules’ twice
- If you want to disable a component, click on that from the entire component list and click on ‘Remove’ from the Actions panel.
- Next, Confirm that you actually want to remove the element by clicking Yes

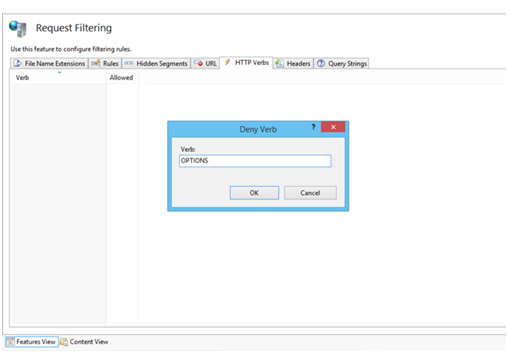
Disable the OPTIONS Method
The OPTIONS method lists the methods available on the server. While this might be beneficial in some ways, it can provide attackers with useful information about what is running on the server:
- Open the IIS Manager
- Select the System Name or change to the specific website you are setting this on
- Open ‘Request Filtering’
- Move to the HTTP Verbs button
- Navigate to the Actions pane, and click on ‘Deny Verb’
- Then click on the Insert ‘OPTIONS’ in the Verb, and click ‘OK’. This will save the modifications you made.
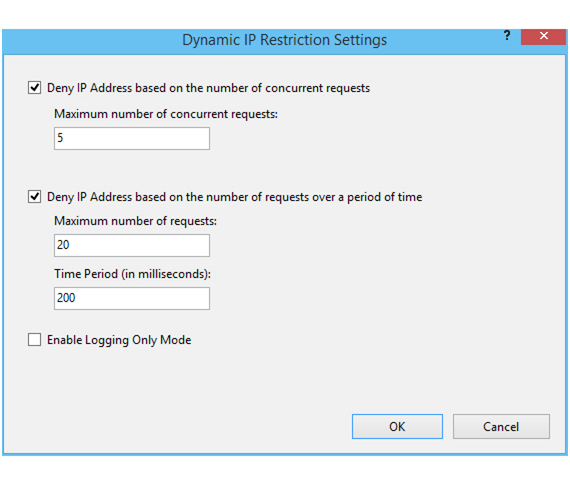
Allow Dynamic IP Restrictions
The Dynamic IP Restrictions module blocks request traffic from IP addresses that make too many requests. This is a useful module for preventing distributed denial of service attacks because of this.
You can configure the module to block both based on concurrent requests and number of requests over time. Depending on the version of IIS you’ll need to install either the “IP Security” feature or the “IP and Domain Restrictions” feature.
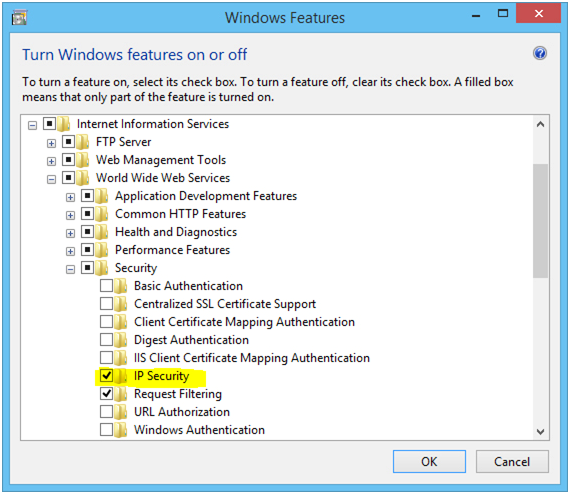
You now have access to the ‘IP Address and Domain Restrictions’ in the Internet Service Manager. Open IIS Manager and do the following:
- Select the System Name or change to the specific website you are setting this on
- Open ‘IP Address and Domain Restrictions’
- In the Actions panel, choose ‘Edit Dynamic Restriction Settings’
- Update the dynamic IP restrictions and click on ‘OK’
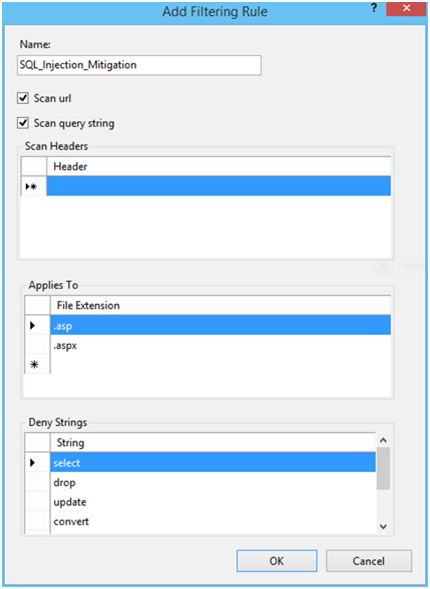
Allow And Set Up Request Filtering Rules
Another thing that will increase the security of your server is to use filtering rules to restrict the type of HTTP requests that the server will process. If there is no reason for your server to accept SQL requests, you can set up a rule to filter these requests out. Open the IIS Manager and follow the example below for ASPX traffic, but understand that this technique can be applied to other types of traffic as well.
- Select the System Name or change to the specific website you are setting this on
- Open ‘Request Filtering’
- Switch to the ‘Rules’ tab
- In the Actions Panel select ‘Add Filtering Rule’
- Set the rules in the screenshot below.
Use Server Logs
Enabling server logging is a great way to monitor your server. With a record of all of the requests that come in, you can check into any network or performance issues and can investigate possible intrusions. IIS logging is set up in the IIS Manager.
You get to it by going to Configure and then Logging in the IIS Manager under the machine or domain you want to set up logging for.
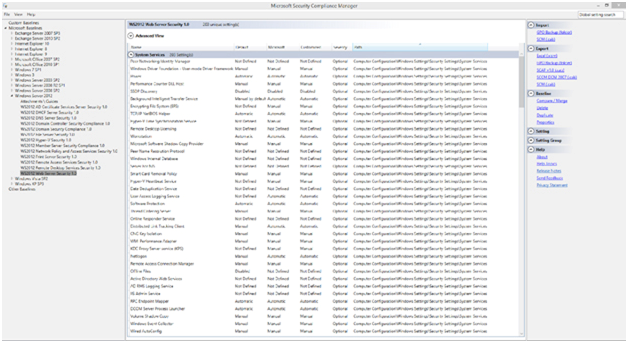
Make use of the Security Configuration Wizard (SCW) and the Security Compliance Manager (SCM)
These are two tools provided by Microsoft to help you test the security of IIS. The Security Configuration Wizard (SCW) scans your system identifying known issues and provides solutions for common issues.
The Security Compliance Manager (SCM) will compare your server’s settings and configuration to known good templates based on best security practices and standards.
Lastly: Update Regularly
Ensure you constantly update your web server to ensure it has all the most recently released features and security enhancements. When you get busy, you can overlook the basics.
The reality of Internet security is that most hacks are the result of people not keeping their system updated. Penetrations from ‘0 day’ attacks are relatively rare compared to the number of known existing threats still circulating across the Internet.
Check out these top 3 Windows hosting services:
0