You should always be concerned about the security of your website infrastructure. It is essential. Your website maintenance must include ways to secure your site infrastructure and PHP applications.
The security of your website infrastructure is essential, and your maintenance plans should include ways to secure both your underlying infrastructure and the applications you have running.
Starting with Internet Information Services 7 (IIS), Microsoft included a number of security features such as dynamic IP restrictions, application pool identities, and SSL support. In this article, we’re going to discuss some ways to secure your PHP applications on the Microsoft Web Platform.
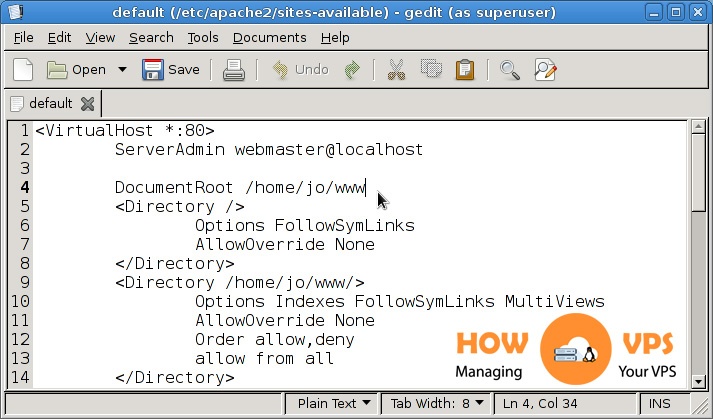
How You Can Secure File Access
We’re going to use Access Control Lists (ACLs) to secure the folder and file structure on IIS. To do this, follow the steps below:
Organize Your Web App Folders
Organize your web app folders and generate new folders for each type of file. Once this is done set the ACLs on each directory and move the files into the folder. Let the files inherit the ACLs from the folder.
It is more difficult to organize and manage a Web app with single ACLs for every file in the system. To give you more control, different separate folders that may require read-write right of entry from non-registered users.
Modify ACLs On The FTP and SMTP Directories
The pre-set configuration of ACLs on the FTP and SMTP directories (C:/inetpub/ftproot and C:/inetpub/mailroot gives everyone complete control. This is not secure, so you should take time to update the entries on the ACL to make your server more secure.
To limit space usage on the IIS volume, put the FTP and SMTP folders on a different volume than the IIS server if you would like to offer support for Everyone (Write). You can also utilize disk quotas to minimize the quantity of data you can write to the FTP and SMTP folders.
Specify The ACLs On The Log Files Created On The IIS
You can do this with (%systemroot%/system32/logfiles) Give administrators and the System (Full Control) and for everyone, give (Read-Write Control).
Disable or Eliminate All Web App Samples Installed On IIS
If there are sample web apps installed disable them or get rid of them. Sample content used by developers isn’t loaded by default and shouldn’t be installed on production servers. The sample apps have a large number of known security risks, for example, IISSamples and IISHelp access virtual directories.
Use Per-Site PHP Configuration
Using the FastCGI handler, you can use a different PHP.ini file for each application mapping. You can modify your PHP setup for each of your users or your apps.
By configuring the PHP.ini file on a basis, you get better control over the system.
Isolate IIS User Accounts and Application Pools
Segregate users and PHP apps with the use of different user accounts and application pools. This keeps users and PHP apps from intruding on each other. Separating user accounts and apps pools can also assist in isolating the PHP crashes to the precise user or app that is the cause of the problem.
Manage NTFS Permissions
Make sure permissions are set for your users. Use the NTFS Deny permissions and only give users access to what they need. If you have separated the user accounts and app pools, you can make it impossible for one user to gain the permissions of another user or application.
Note that is is more common to exclude users from ACLs versus setting Deny on specific files and folders. Plan your permission structure ahead of time and backup everything before making changes.
Make Use Of URL Rewriting
Use URL rewriting to secure your server. Instead of just storing the Session ID on the URL, store it in a cookie instead. Then generate a new token on the URL. If the next request from the server does not include the new token, the server can ignore it.
Alter Your Configuration Settings
You can alter PHP settings to stiffen the security of a PHP installation. This assists to keep the Website secure and safe from attacks from unscrupulous elements. The Php.ini file stipulates the arrangement of settings used by PHP on your Website. The Php.ini file establishes the limit of permission granted to the PHP scripts and also stipulates the actions that the scripts are prevented from performing.
Limit Permissions To PHP Extensions
Only grant permissions to the PHP extensions that would be utilized by your apps. Some PHP commands, like register_globals and allow_url_fopen, can cause security risks. You must, therefore, disable them if you can. Additionally, you need to turn off the expose_php command to prevent PHP from disclosing that it is set up on your server.
Enable Only Functions and Classes Used By Your Apps
Modify your PHP settings to enable just the functions and classes utilized by your application. Utilize the disable_functions and disable_classes PHP commands to get a listing of comma-separated functions and classes that you plan to disable.
Then, place a boundary on the command: the max_execution_time, max_input_time, memory_limit, post_max_size and upload_max_filesize to just what you require and what your server can manage.
Utilize Request Filters
Place limits on what kind of HTTP requests. Most PHP applications only need GET, HEAD, and POST capabilities. You can use a security tool called URLScan to filter out other types of HTTP requests preventing harmful requests from running. This tool comes with IIS and is installed as part of the ISAPI (Internet Server Application Programming Interface) filter.
It can also scan for known malicious traffic patterns and prevents the traffic from being processed by the server. This makes request filtering with URLScan a great way to improve your system security.
Check out these top 3 Best web hosting services
0